The Great Resignation hit the workforce hard, especially in fields that experienced extreme increases in demand because of COVID-19, accordingto Harvard Business Review. Many organizations had to halt or delay projects, focusing their energy on...
Three Tips for Successfully Navigating the Great Resignation
by
Laura Gelb |
March
22,
2022 |
IT Management,
Process,
IT Infrastructure,
Business Continuity,
Remote Work,
IT Services,
IT Managed Services,
Business Processes ,
Teamwork,
Business
How to Move Files in Microsoft Sharepoint Using Power Automate
by
Bethany Schaumann |
March
15,
2022 |
Cloud,
IT Management,
IT Infrastructure,
IT Support,
Microsoft Office 365,
MSP,
IT Services,
IT Managed Services,
IT Strategy,
microsoft
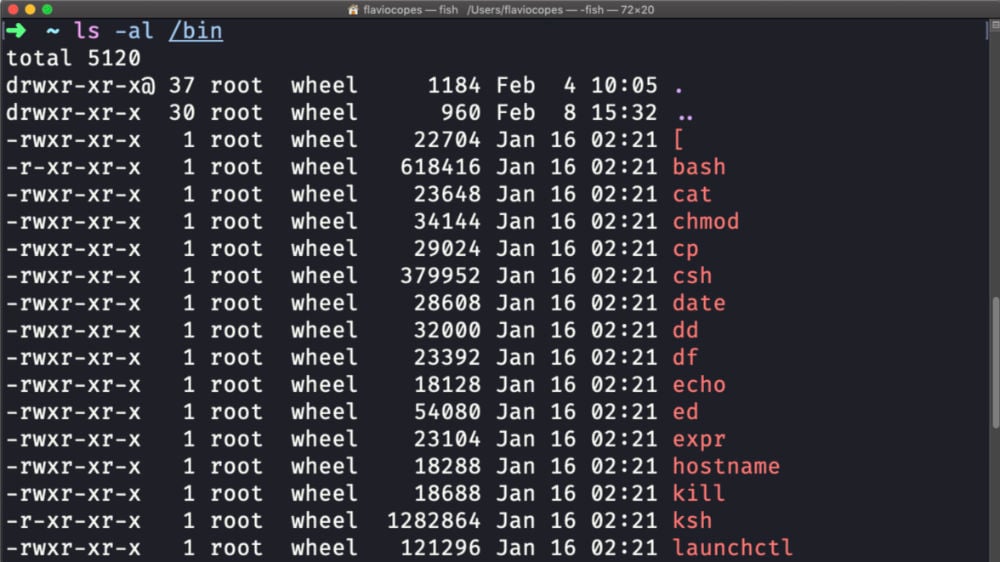
How To Calculate UNIX File Permissions
by
Russell Poovey |
March
01,
2022 |
Cloud,
IT Management,
Security,
IT Infrastructure,
IT Support,
MSP,
IT Services,
IT Managed Services,
IT Strategy,
windows
Introduction
Unix file permissions can seem a bit daunting to everyone. This guide will help to have a solid grasp on setting the correct permissions for all UNIX file systems. Covering both Linux and Mac distributions.
Business Empowerment: Where Information Technology Intersects Growth
by
Cristina McIntire |
February
22,
2022 |
IT Management,
IT Infrastructure,
IT Support,
IT Services,
it consulting,
Information Technology
When individuals contemplate IT they typically reflect on the ways in which they have been exposed and impacted by IT services. Often services like setting up computers and fixing printers come to mind. These services frequently equate to “IT help”...
SSSD Linux Active Directory Authentication: Joining a Domain Without VPN
by
Russell Poovey |
February
15,
2022 |
Cloud,
IT Management,
Security,
IT Infrastructure,
IT Support,
MSP,
IT Services,
IT Managed Services,
IT Strategy,
windows,
Azure
We have a few earlier blog posts on setting up Linux based Samba file shares with Active Directory authentication.Similarly, there are many documents on the Internet on configuring LDAP authentication to Active Directory.However, very little has...
-1.png?width=350&height=117&name=iuvo_logo_blue_Transparent%20(1)-1.png)