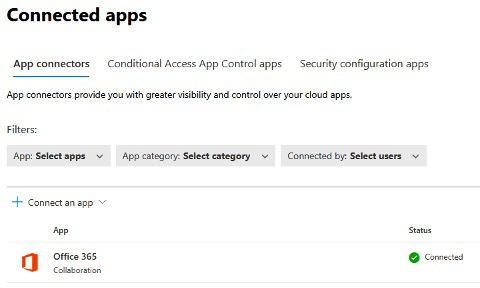
Businesses spend a lot of time creating, provisioning and deactivating users—especially amid the proliferation of hybrid work. Unfortunately, many organizations are relying on clunky manual processes to do this, which fail to fully embrace current...
Modern Workplace: Reducing Risk and Improving Business Practices
Business Benefits of a Strong IT Infrastructure
The IT infrastructure is the foundation of your company, and it's critical to the everyday operations of your business. Without it, you can't keep up with customer service requests or make progress on key initiatives. But when it's working properly,...
Protecting Your Data with Microsoft Sensitivity Labels
Table of Contents: 1. Microsoft Labels and Information Protection2. Sensitivity Labels Overview3. Using MCAS to apply Microsoft Sensitivity Labels4. Configuration5. Integration with Microsoft Copilot6. Licensing Requirements7. Management 8....
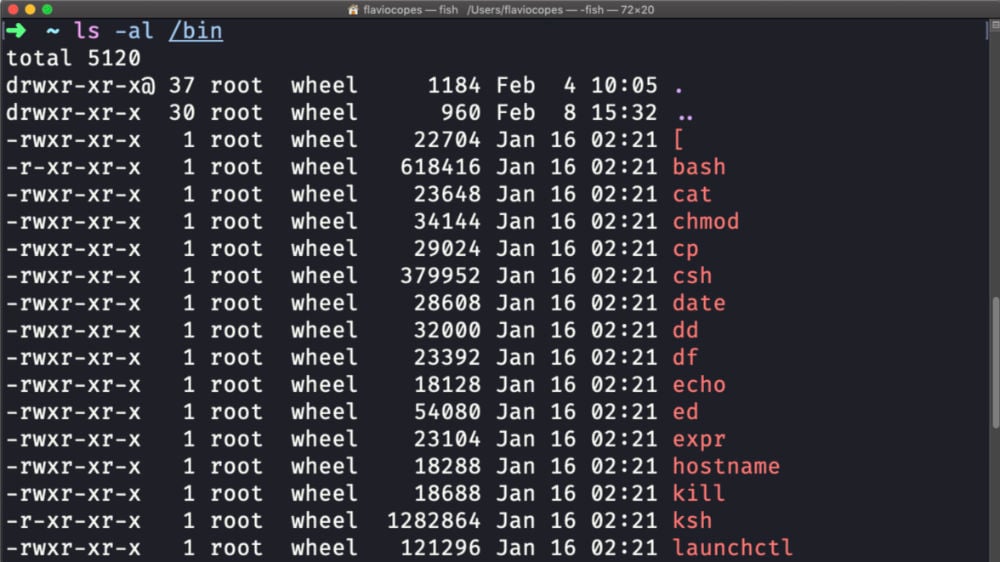
How To Calculate UNIX File Permissions
Introduction
Unix file permissions can seem a bit daunting to everyone. This guide will help to have a solid grasp on setting the correct permissions for all UNIX file systems. Covering both Linux and Mac distributions.
SSSD Linux Active Directory Authentication: Joining a Domain Without VPN
We have a few earlier blog posts on setting up Linux based Samba file shares with Active Directory authentication.Similarly, there are many documents on the Internet on configuring LDAP authentication to Active Directory.However, very little has...
-1.png?width=350&height=117&name=iuvo_logo_blue_Transparent%20(1)-1.png)