Port forwarding is a critical feature of any network firewall. The ability to provide a service to the Internet requires being able to forward ports from one interface of a firewall to another interface. Sometimes these services are on dedicated IP addresses, other times the addresses are shared and mostly using some type of Network Address Translation (NAT).
We will focus on port forwarding on a Cisco ASA configured in routed mode, using a Bridged Virtual Interface (BVI), using Cisco’s ASDM GUI administration tool. Our test network is setup as follows:
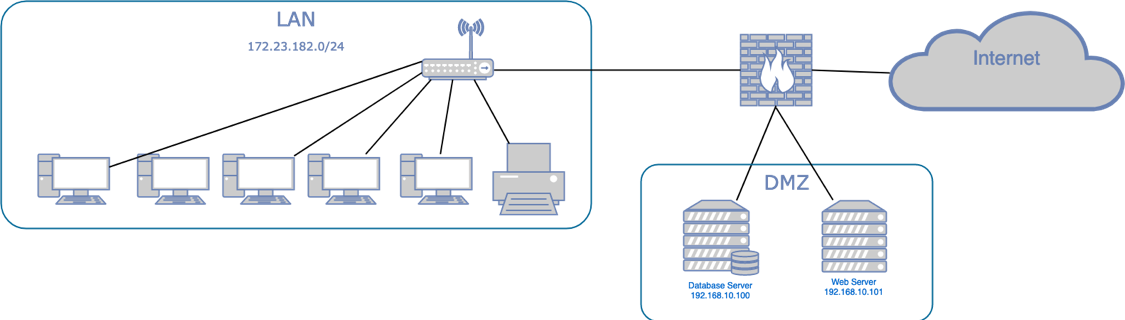
A Cisco ASA with four interfaces in use, one connected to the Internet, one connected to a LAN switch, one connected to a DMZ web server, and one with a DMZ database server. We need to allow HTTP and HTTPS from the DMZ web server to the Internet, but the DMZ database server must be protected.
Initial Setup
To start, we need to confirm the firewall is in routed mode, this is on by default, but still worth checking. Once connected to the ASA with ASDM the Home button in the top left of the window should be selected, and the Device Dashboard shown. It should look similar to what is show below.
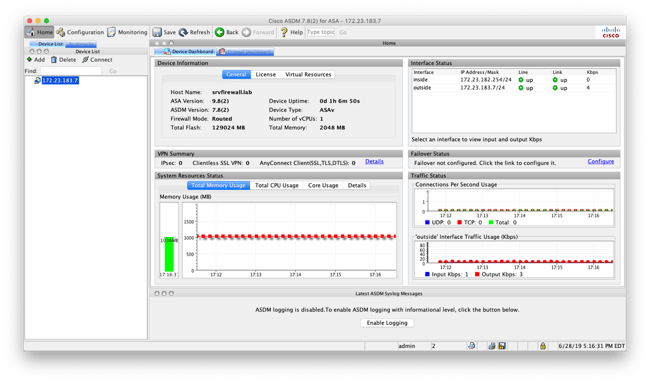
Firewall Mode should be Routed, the firewall mode is Transparent and in production, we do not recommend changing the mode, rather configure port forwarding as it is.
Often the quickest and easiest approach is to forward to servers on the LAN. This should not be done. If outside access to internal servers is required use some type of proxy inside a DMZ. We will outline how to setup a DMZ and then forward outside requests to hosts within the DMZ.
Cisco DMZ Setup
We start with creating the BVI interface, by going into Cisco firewall DMZ Configuration on ASDM, selecting Device Setup, Interface Settings, and Interfaces.
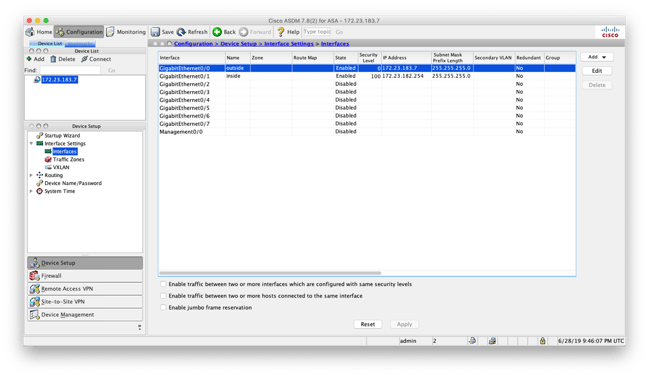
Select Add in the top right corner and choose Bridge Group Interface, then we will configure the interface for the DMZ network.
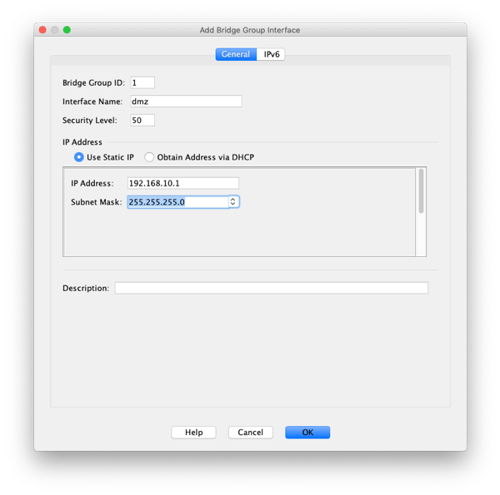
Now we will add the two physical interfaces that will support our database and web servers to the Bridge Group. In our case we are using GigabitEthernet0/2 and GigabitEthernet0/3.
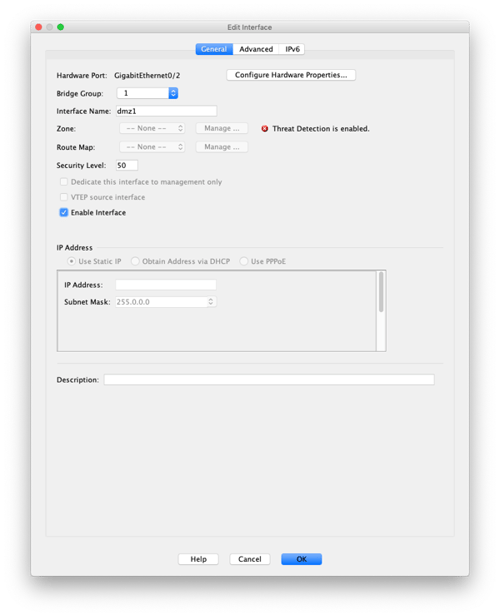
The configuration looks like this
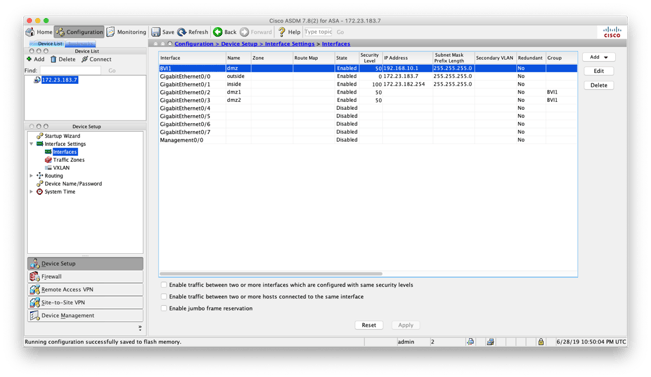
We now make sure the web server is connected to GigabitEthernet0/2 and the database server to GigabitEthernet0/3. Confirm network connectivity between the web server and database server. If there are connectivity issues, confirm the interfaces are enabled, and have the correct bridge group selected.
Port Forwarding
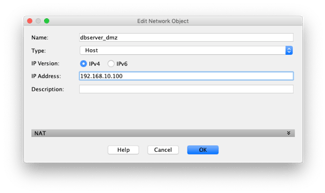
Now that the DMZ is setup and configured, we need to enable the port forwarding. In our case we will use a second outside IP address for the NAT address. We have setup the outside network as 172.23.183.0/24 which is still a private network which we use for testing. The firewall has an outside address of 172.23.183.7 and we will use 172.23.183.8 for the web server. To keep everything well organized we will create network objects for both the web server internal and external addresses, and the internal address of the database server. Click on Firewall in the lower left of the ASDM, and then Add in the top right, and select Network Object.
We should create the objects representing the addresses of our servers for.
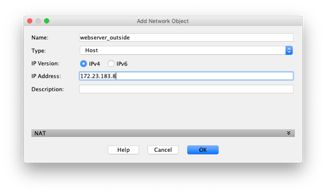 |
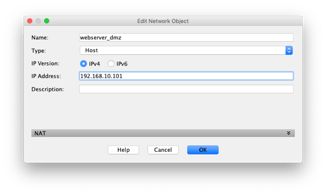 |
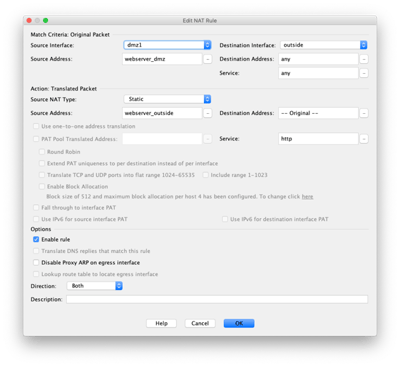
Now we will configure the static NAT entry for the webserver. Select NAT Rules on the left side of the ASDM Window and select Add at the top middle.
 |
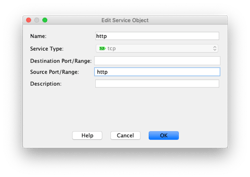 |
We need to add a service, for both http and https. We also need NAT rules for each service. When complete is should look like this:
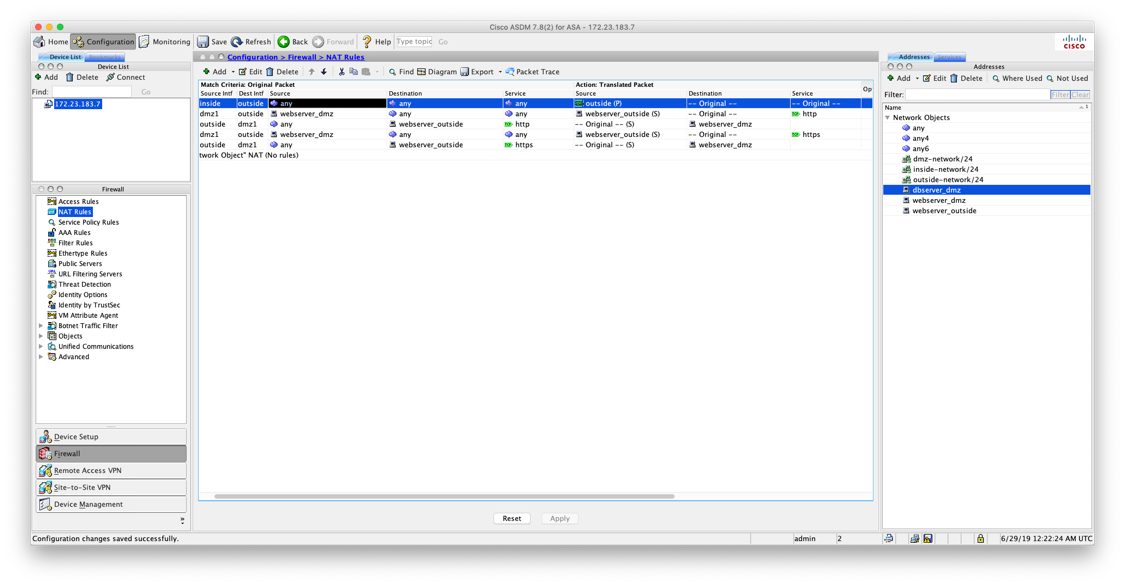
Now we need to configure access rules to allow the inbound connections. Select Access Rules on the left side of the ASDM window, and select Add. Unlike with the NAT rules, we can use a single access rule for both http and https.
When complete it should look like this:
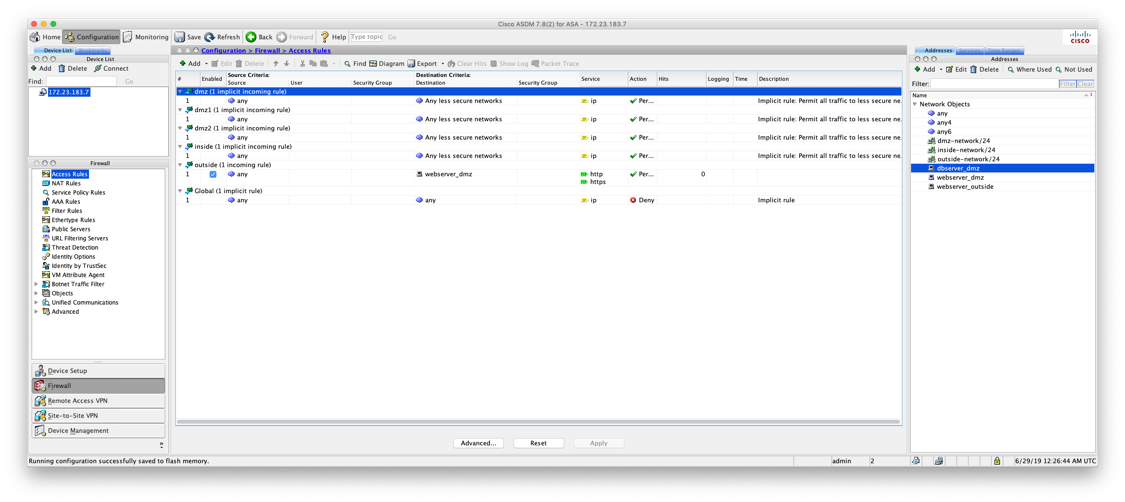
At this point your webserver will respond to connections requests from the outside interface (Internet).
The completed firewall configuration is:
hostname srvfirewall
domain-name lab
enable password $sha512$5000$W8zjbSWKdd5L6uGeNpG5Yw==$OMBBh/TQlXOKlcAIvoBBng== pbkdf2
names
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 172.23.183.7 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 172.23.182.254 255.255.255.0
!
interface GigabitEthernet0/2
bridge-group 1
nameif dmz1
security-level 50
!
interface GigabitEthernet0/3
bridge-group 1
nameif dmz2
security-level 50
!
interface GigabitEthernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/6
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/7
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
management-only
shutdown
no nameif
no security-level
no ip address
!
interface BVI1
nameif dmz
security-level 50
ip address 192.168.10.1 255.255.255.0
!
ftp mode passive
dns server-group DefaultDNS
domain-name lab
object network webserver_outside
host 172.23.183.8
object network webserver_dmz
host 192.168.10.101
object service http
service tcp source eq www
object network dbserver_dmz
host 192.168.10.100
object service https
service tcp source eq https
object-group service DM_INLINE_TCP_1 tcp
port-object eq www
port-object eq https
access-list outside_access_in extended permit tcp any object webserver_dmz object-group DM_INLINE_TCP_1
pager lines 23
mtu outside 1500
mtu inside 1500
mtu dmz1 1500
mtu dmz2 1500
no failover
no monitor-interface dmz
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 8192
nat (inside,outside) source dynamic any interface
nat (dmz1,outside) source static webserver_dmz webserver_outside service any http
nat (dmz1,outside) source static webserver_dmz webserver_outside service any https
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 172.23.183.1 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication login-history
http server enable
http 172.23.183.0 255.255.255.0 outside
no snmp-server location
no snmp-server contact
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpoint _SmartCallHome_ServerCA
no validation-usage
crl configure
crypto ca trustpool policy
auto-import
crypto ca certificate chain _SmartCallHome_ServerCA
certificate ca 513fb9743870b73440418d30930699ff
30820538 30820420 a0030201 02021051 3fb97438 70b73440 418d3093 0699ff30
0d06092a 864886f7 0d01010b 05003081 ca310b30 09060355 04061302 55533117
30150603 55040a13 0e566572 69536967 6e2c2049 6e632e31 1f301d06 0355040b
13165665 72695369 676e2054 72757374 204e6574 776f726b 313a3038 06035504
0b133128 63292032 30303620 56657269 5369676e 2c20496e 632e202d 20466f72
20617574 686f7269 7a656420 75736520 6f6e6c79 31453043 06035504 03133c56
65726953 69676e20 436c6173 73203320 5075626c 69632050 72696d61 72792043
65727469 66696361 74696f6e 20417574 686f7269 7479202d 20473530 1e170d31
33313033 31303030 3030305a 170d3233 31303330 32333539 35395a30 7e310b30
09060355 04061302 5553311d 301b0603 55040a13 1453796d 616e7465 6320436f
72706f72 6174696f 6e311f30 1d060355 040b1316 53796d61 6e746563 20547275
7374204e 6574776f 726b312f 302d0603 55040313 2653796d 616e7465 6320436c
61737320 33205365 63757265 20536572 76657220 4341202d 20473430 82012230
0d06092a 864886f7 0d010101 05000382 010f0030 82010a02 82010100 b2d805ca
1c742db5 175639c5 4a520996 e84bd80c f1689f9a 422862c3 a530537e 5511825b
037a0d2f e17904c9 b4967719 81019459 f9bcf77a 9927822d b783dd5a 277fb203
7a9c5325 e9481f46 4fc89d29 f8be7956 f6f7fdd9 3a68da8b 4b823341 12c3c83c
ccd6967a 84211a22 04032717 8b1c6861 930f0e51 80331db4 b5ceeb7e d062acee
b37b0174 ef6935eb cad53da9 ee9798ca 8daa440e 25994a15 96a4ce6d 02541f2a
6a26e206 3a6348ac b44cd175 9350ff13 2fd6dae1 c618f59f c9255df3 003ade26
4db42909 cd0f3d23 6f164a81 16fbf283 10c3b8d6 d855323d f1bd0fbd 8c52954a
16977a52 2163752f 16f9c466 bef5b509 d8ff2700 cd447c6f 4b3fb0f7 02030100
01a38201 63308201 5f301206 03551d13 0101ff04 08300601 01ff0201 00303006
03551d1f 04293027 3025a023 a021861f 68747470 3a2f2f73 312e7379 6d63622e
636f6d2f 70636133 2d67352e 63726c30 0e060355 1d0f0101 ff040403 02010630
2f06082b 06010505 07010104 23302130 1f06082b 06010505 07300186 13687474
703a2f2f 73322e73 796d6362 2e636f6d 306b0603 551d2004 64306230 60060a60
86480186 f8450107 36305230 2606082b 06010505 07020116 1a687474 703a2f2f
7777772e 73796d61 7574682e 636f6d2f 63707330 2806082b 06010505 07020230
1c1a1a68 7474703a 2f2f7777 772e7379 6d617574 682e636f 6d2f7270 61302906
03551d11 04223020 a41e301c 311a3018 06035504 03131153 796d616e 74656350
4b492d31 2d353334 301d0603 551d0e04 1604145f 60cf6190 55df8443 148a602a
b2f57af4 4318ef30 1f060355 1d230418 30168014 7fd365a7 c2ddecbb f03009f3
4339fa02 af333133 300d0609 2a864886 f70d0101 0b050003 82010100 5e945649
dd8e2d65 f5c13651 b603e3da 9e7319f2 1f59ab58 7e6c2605 2cfa81d7 5c231722
2c3793f7 86ec85e6 b0a3fd1f e232a845 6fe1d9fb b9afd270 a0324265 bf84fe16
2a8f3fc5 a6d6a393 7d43e974 21913528 f463e92e edf7f55c 7f4b9ab5 20e90abd
e045100c 14949a5d a5e34b91 e8249b46 4065f422 72cd99f8 8811f5f3 7fe63382
e6a8c57e fed008e2 25580871 68e6cda2 e614de4e 52242dfd e5791353 e75e2f2d
4d1b6d40 15522bf7 87897812 816ed94d aa2d78d4 c22c3d08 5f87919e 1f0eb0de
30526486 89aa9d66 9c0e760c 80f274d8 2af8b83a ced7d60f 11be6bab 14f5bd41
a0226389 f1ba0f6f 2963662d 3fac8c72 c5fbc7e4 d40ff23b 4f8c29c7
quit
telnet timeout 5
ssh stricthostkeycheck
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
dynamic-access-policy-record DfltAccessPolicy
username admin password $sha512$5000$XJSawtOyOc99xLar+yD81g==$pMrkut3UItMMQm6wOZurag== pbkdf2
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
profile License
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination transport-method http
While many people prefer using the command interface for configuring Cisco ASAs, it is also possible to use ASDM for more complex configurations. If this is something you would like assistance with or would like to discuss, an iuvo Technologies network engineer would be happy to assist. Get a FREE IT assessment today!
-1.png?width=350&height=117&name=iuvo_logo_blue_Transparent%20(1)-1.png)