Introduction
Often legacy systems use Tomcat as the foundation for a web-based user interface. Sometimes the vendor may no longer support the system, or even if supported, will not support basic security enhancing changes such as using https, or if https is supported, disabling vulnerable protocols such as SSLv3, TLS 1.0/1.1. Sometimes, Tomcat is still running on the default port 8080, which can cause confusion with end users as well. For these, and other reasons, we will look at the setup of a reverse http proxy through Microsoft Internet Information Server (IIS) to address this.
While this blog focuses on using Microsoft IIS, there are a number of other applications that also support reverse proxies, we are choosing IIS because Tomcat will often run on a Windows server, and this can provide an “all in one” solution. Other approaches may work better in other situations.
Assumptions
We will not go into the setup and configuration of Tomcat but will assume it is running on the same system as the reverse proxy and listening on port 8080, and port 80 is free. We also assume the system has internet access so the needed software can be downloaded.
Pre-Requisites
Unfortunately, IIS doesn’t support reverse proxy “out of the box”, a few additional packages (available from Microsoft for free) are required.
- IIS and ASP.NET installed
- URL Rewrite Module installed (this will be downloaded)
- Application Request Routing installed (this will be downloaded)
Installation
IIS Installation
Starting with installing Microsoft IIS on the server:
- Open Server Manager
- Select Manage
- Add Roles and Features (confirm you are on the correct system)
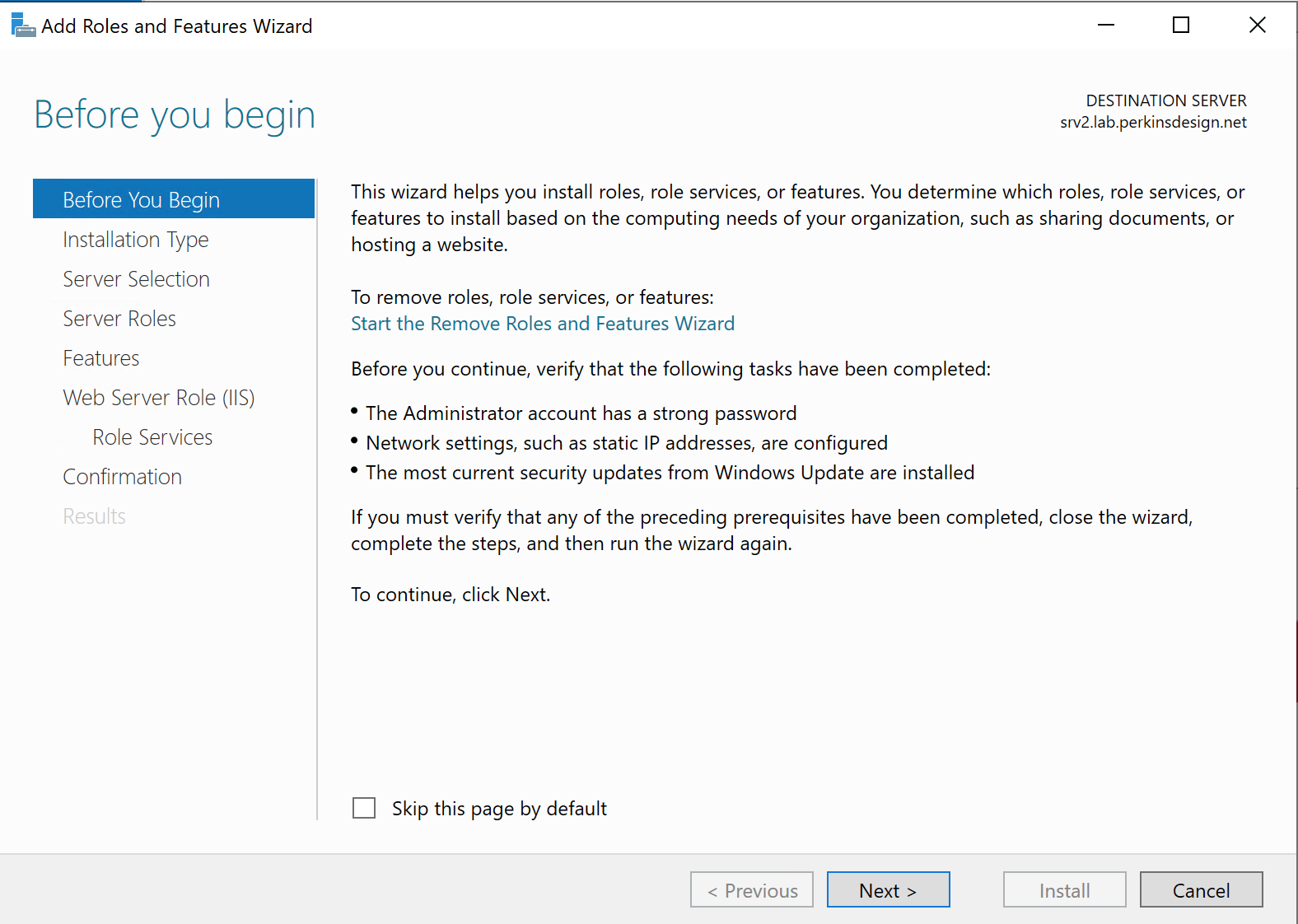
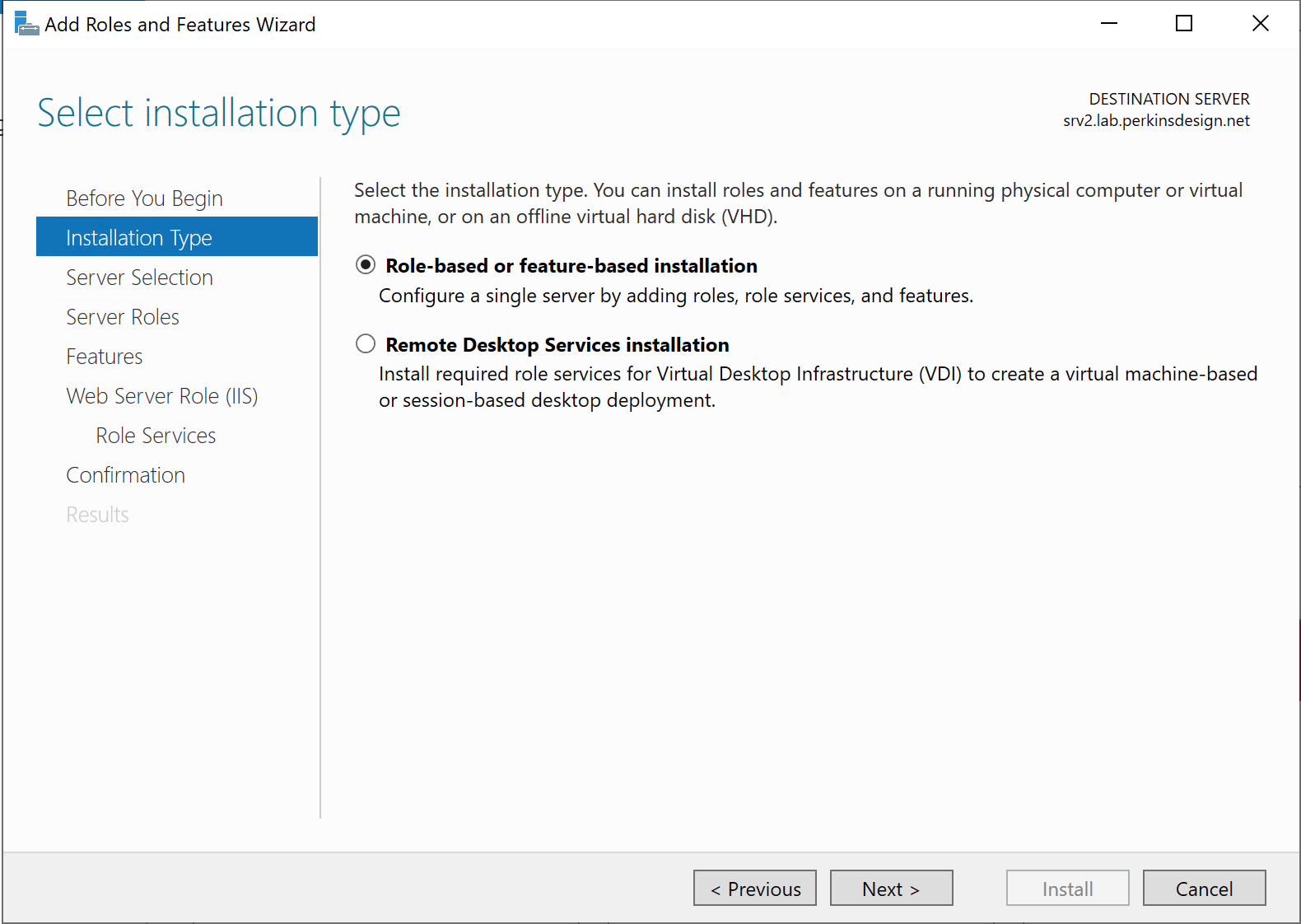
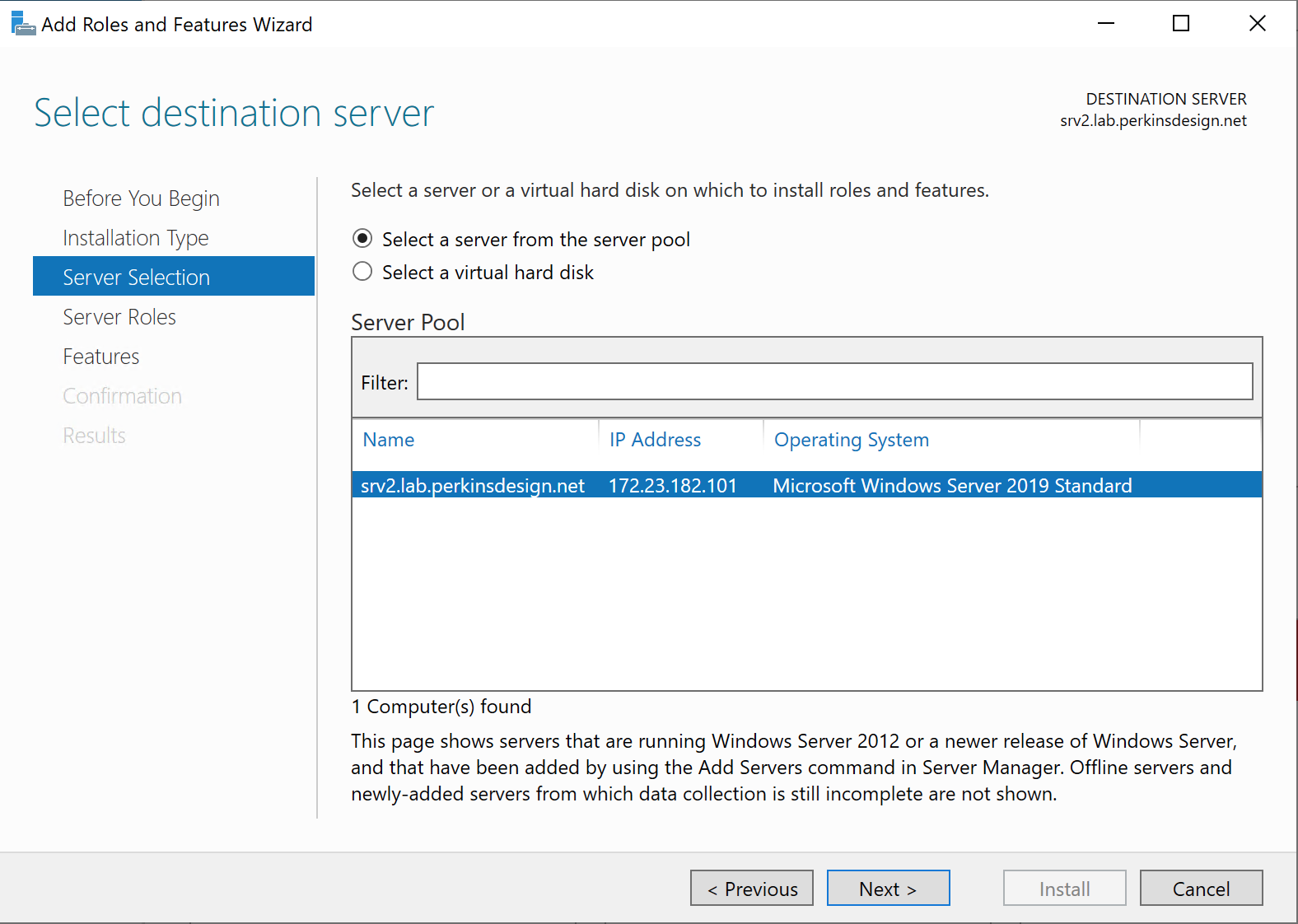
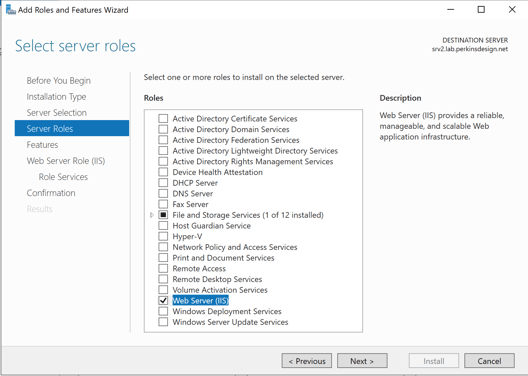
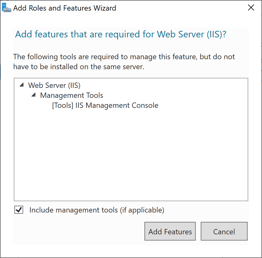
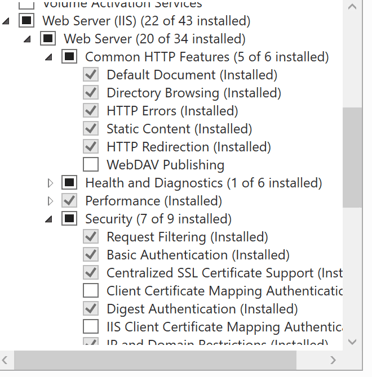
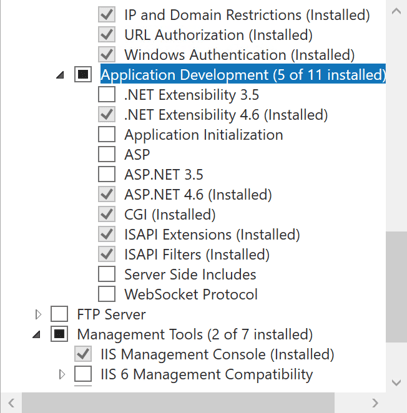
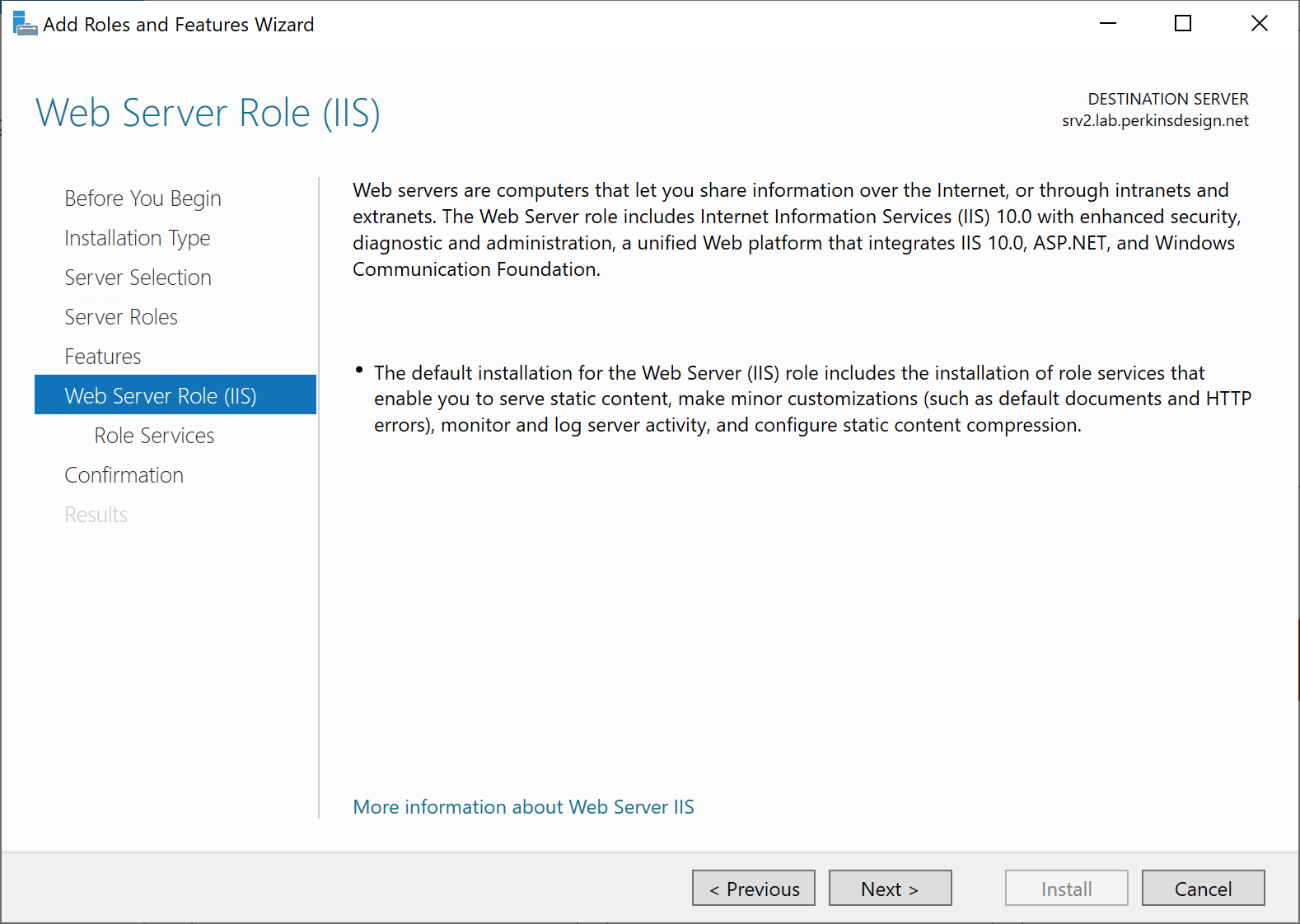
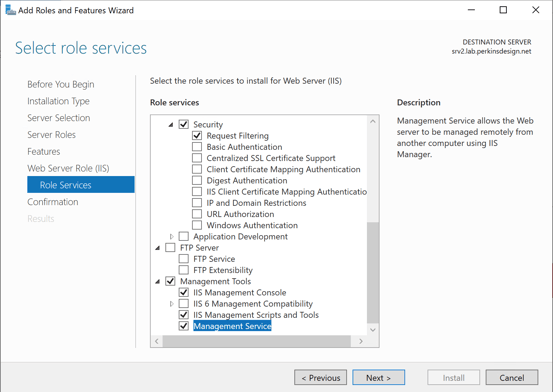
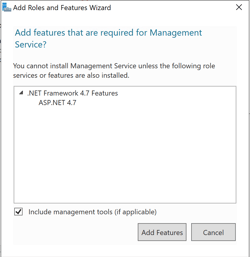
At this point the installation of IIS can start, and once complete it is a good idea to confirm that IIS is reachable via port 80. Note, the installation should open port 80 in the Windows Defender Firewall automatically.
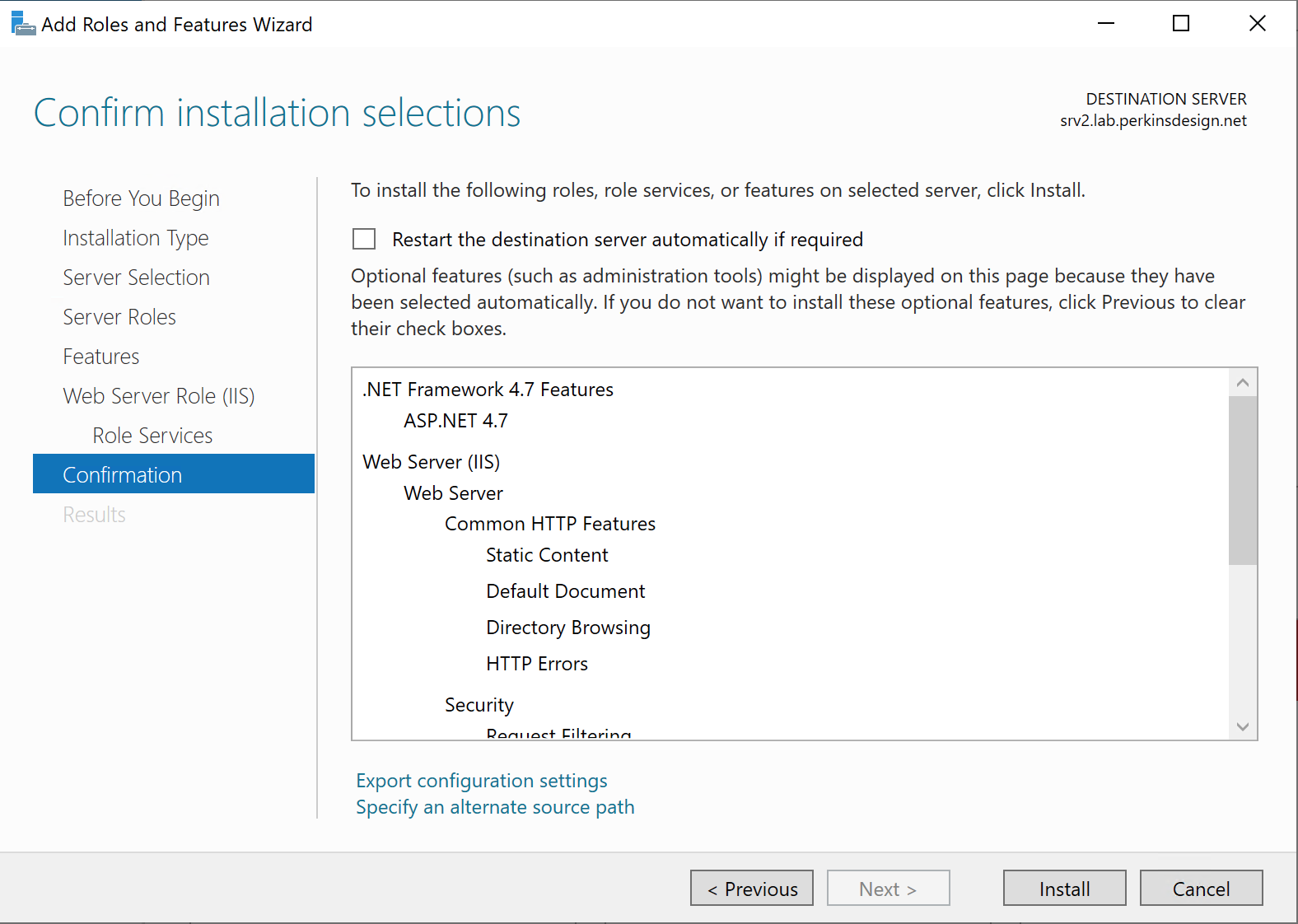
Installing URL Rewrite and Application Request Routing
Both the URL Rewrite module and the Application Request Routing module can be installed from Microsoft’s Web Platform Installer found at:
https://www.iis.net/downloads/microsoft/web-platform-installer
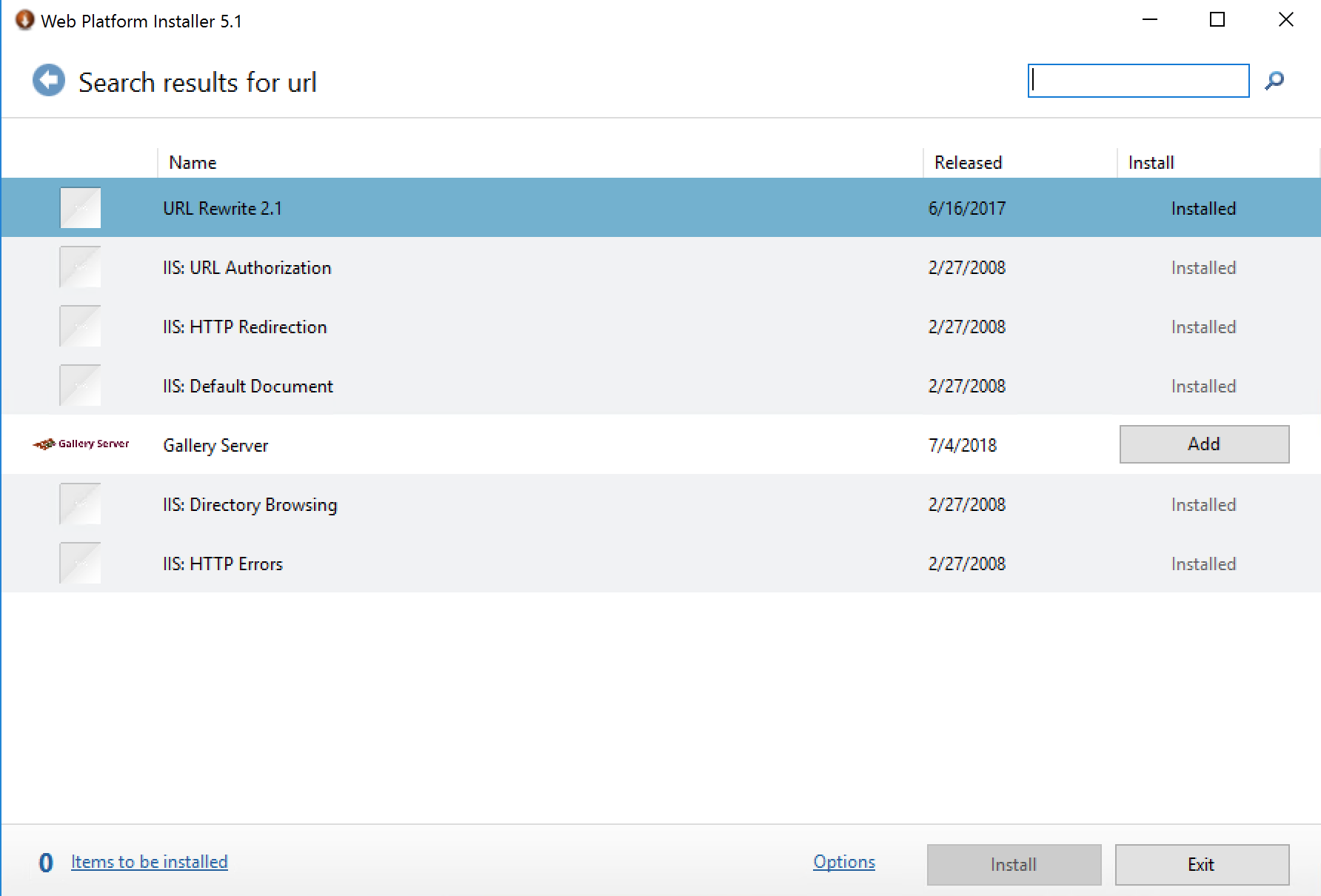
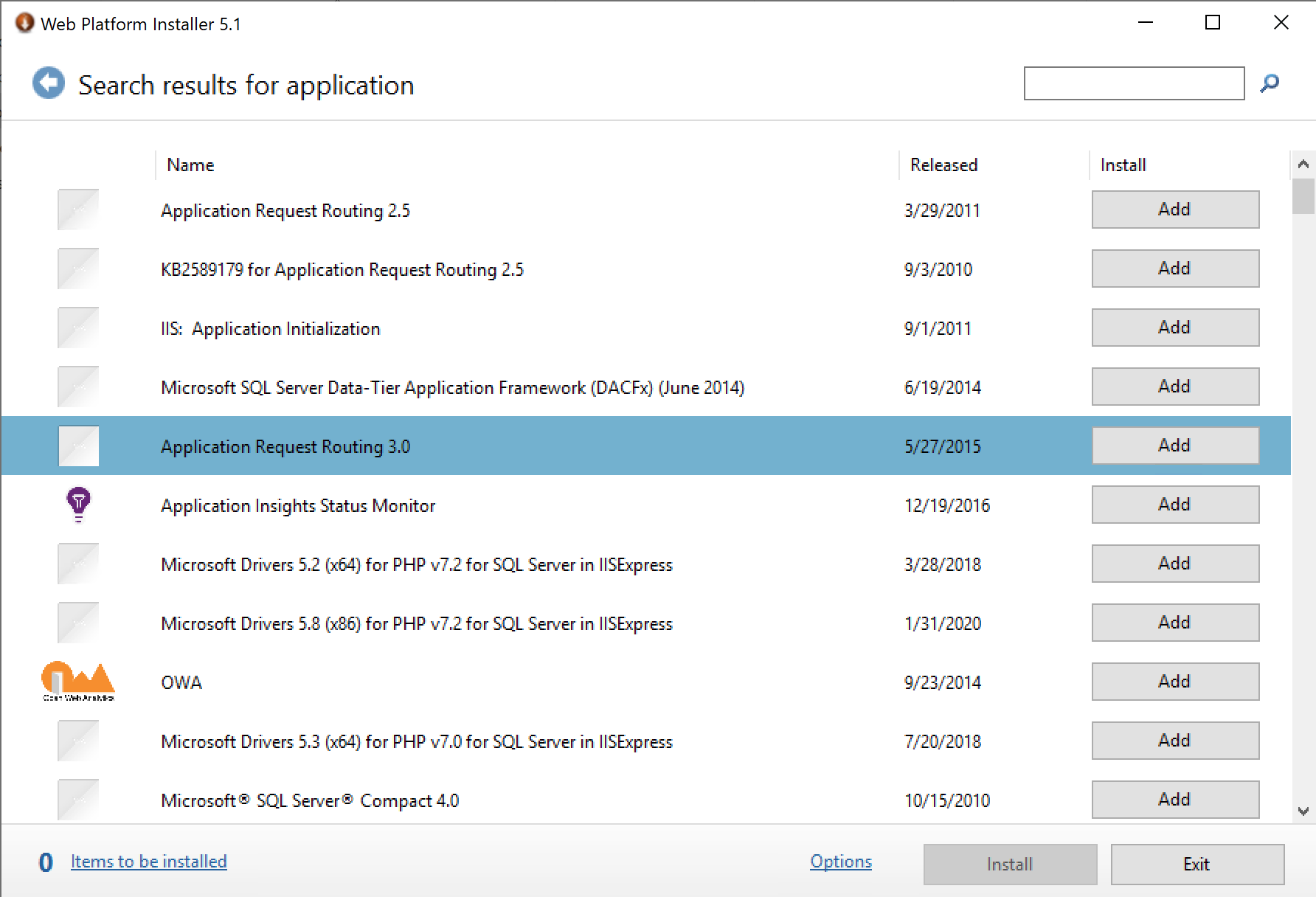
Depending on the version of Windows Server, Application Request Routing 2.5 or 3.0 may be needed.
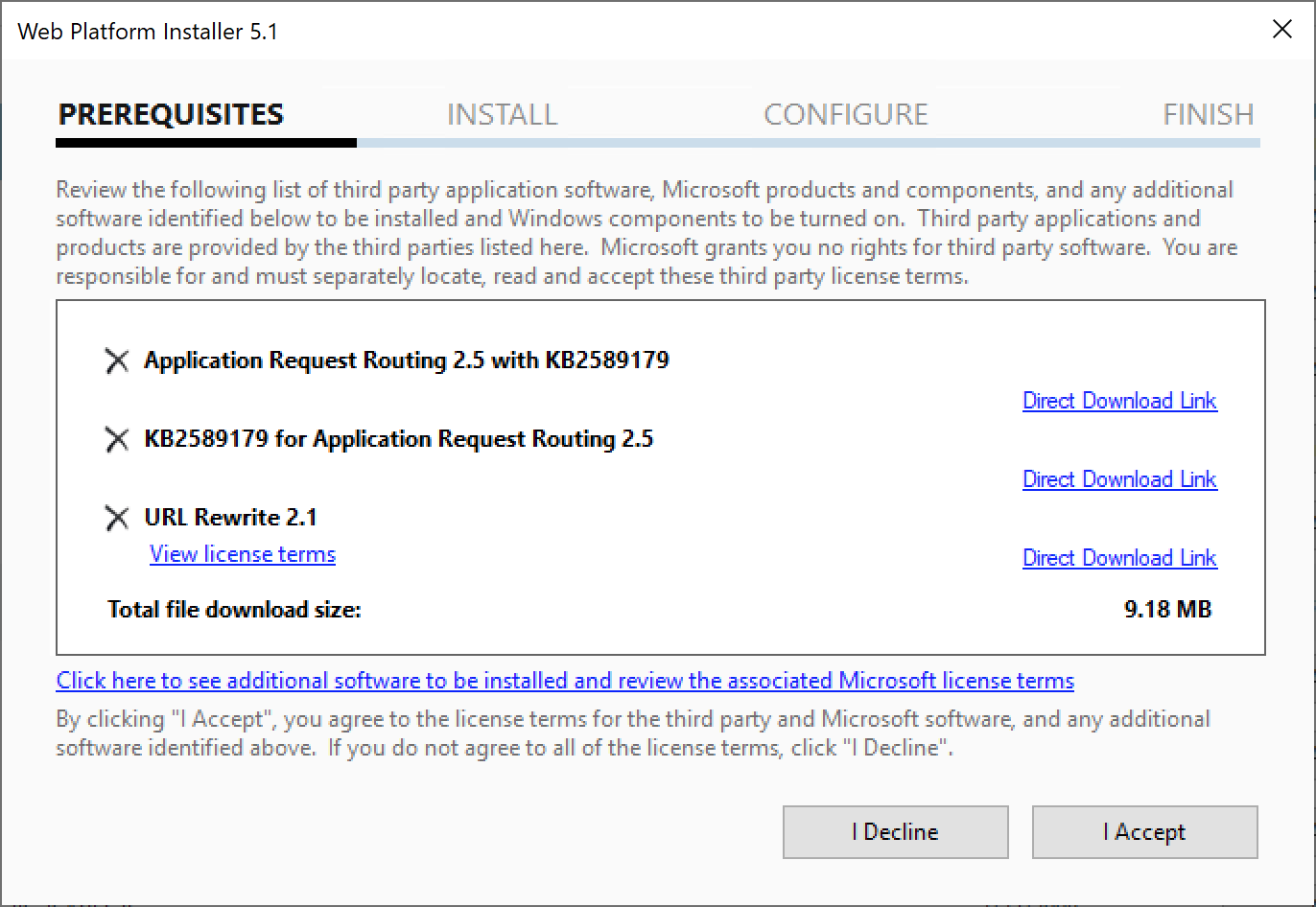
Configuring the Reverse Proxy
Once the required software is installed, open IIS Manager, highlight the current server and select Application Request Routing.
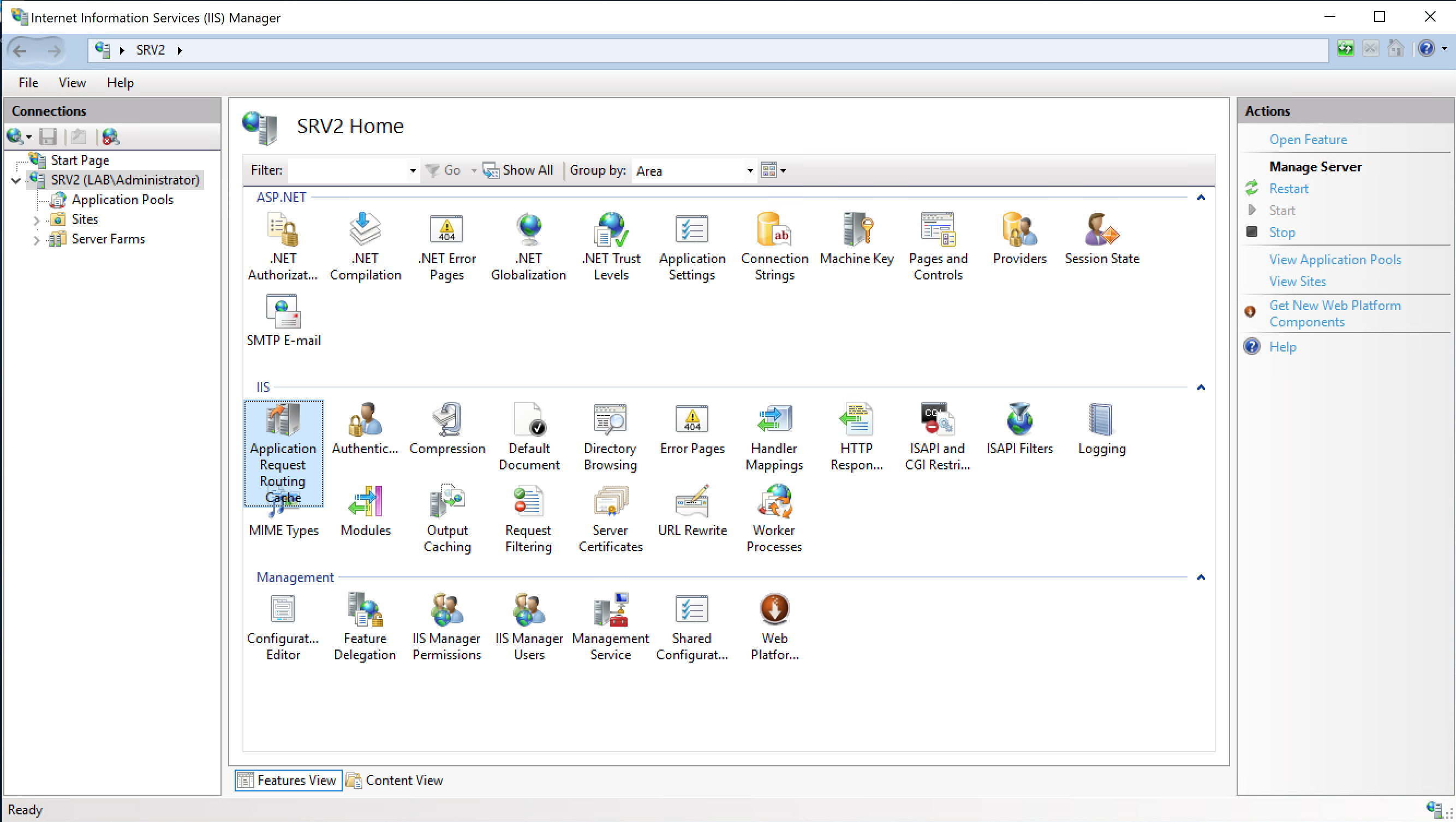
Click on Server Proxy Settings and Check “Enable proxy”
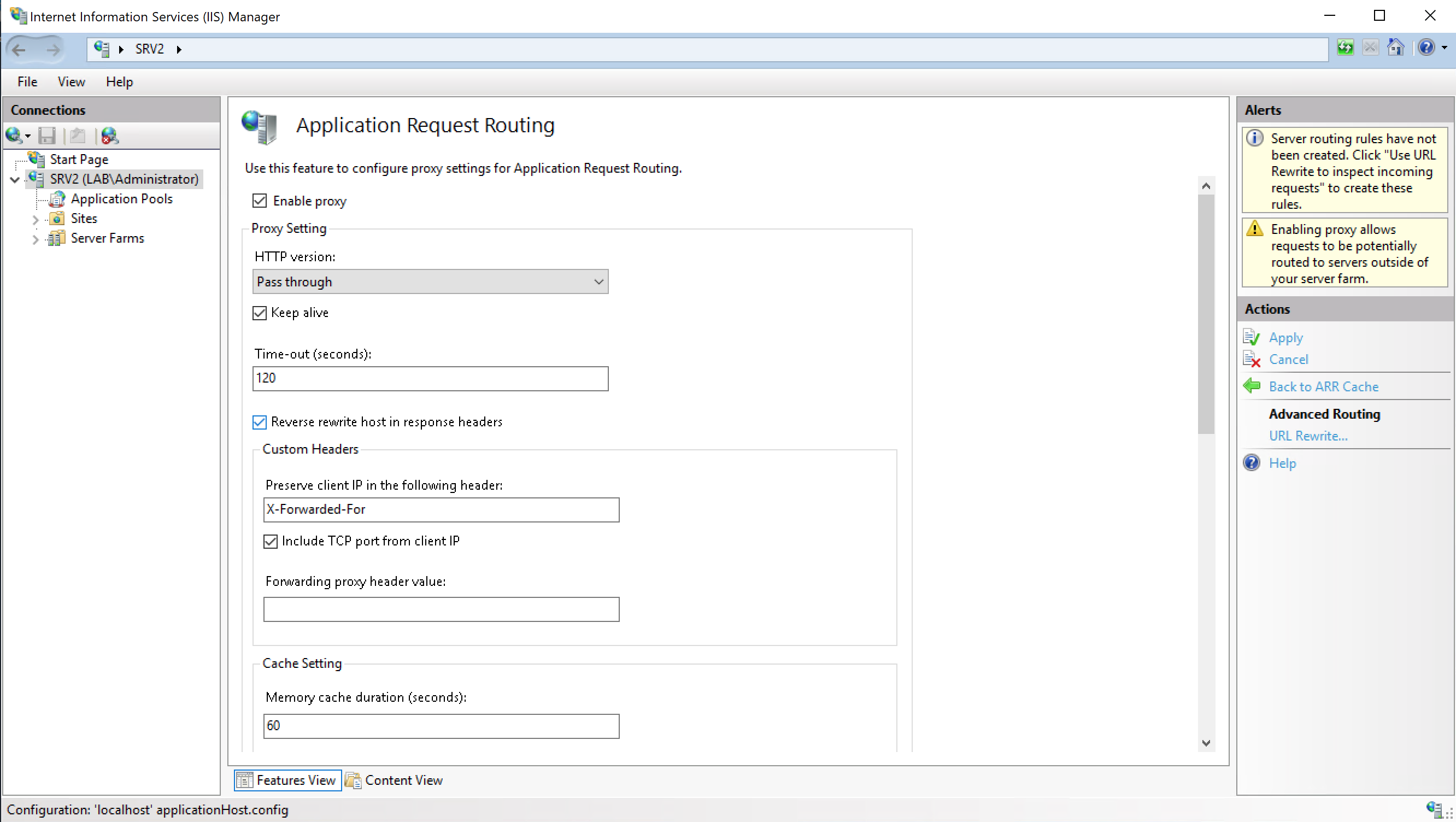
Then go to the Default Web Site and select URL Rewrite, and then choose Add Rule(s)…
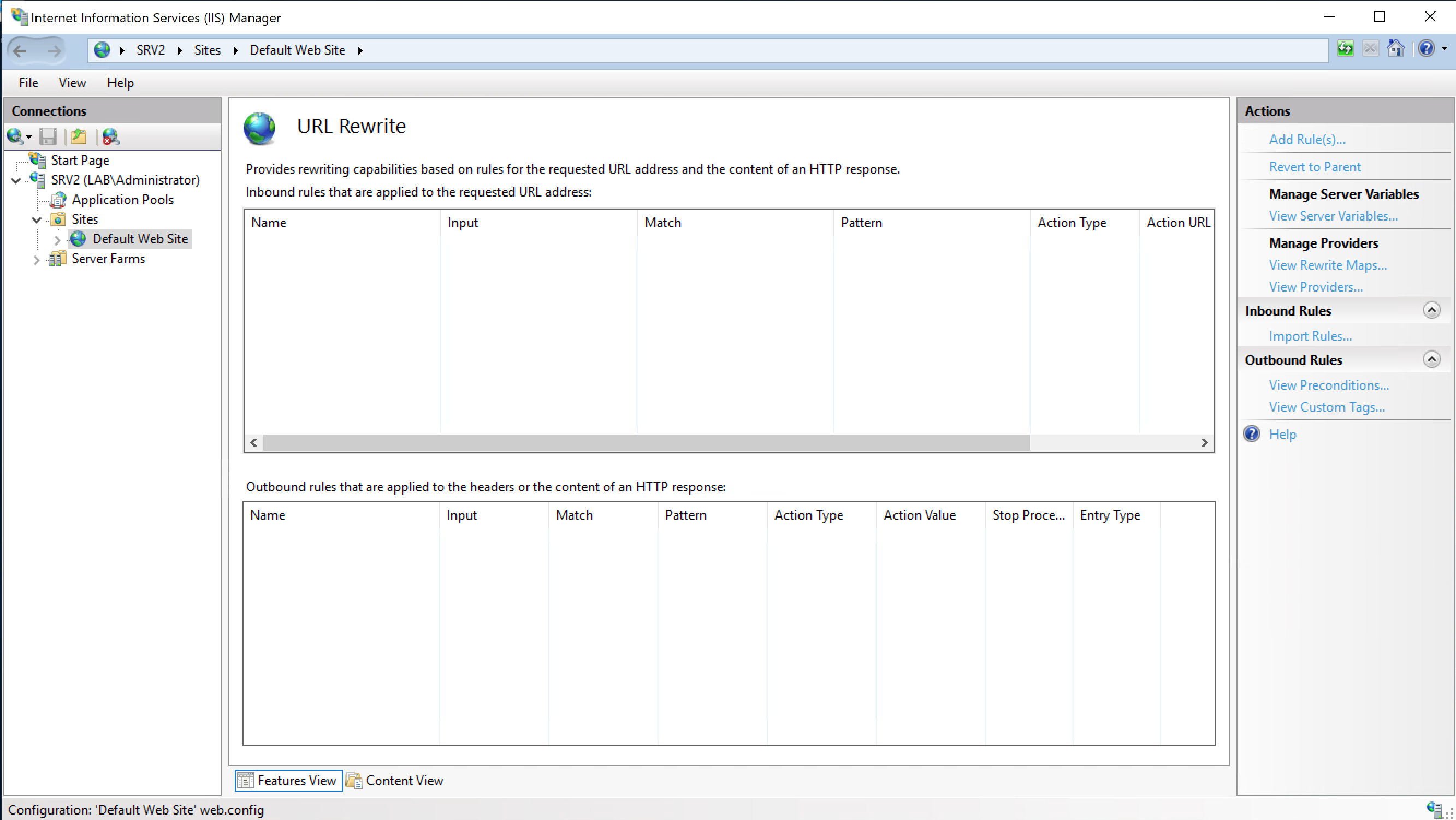
Select Reverse Proxy
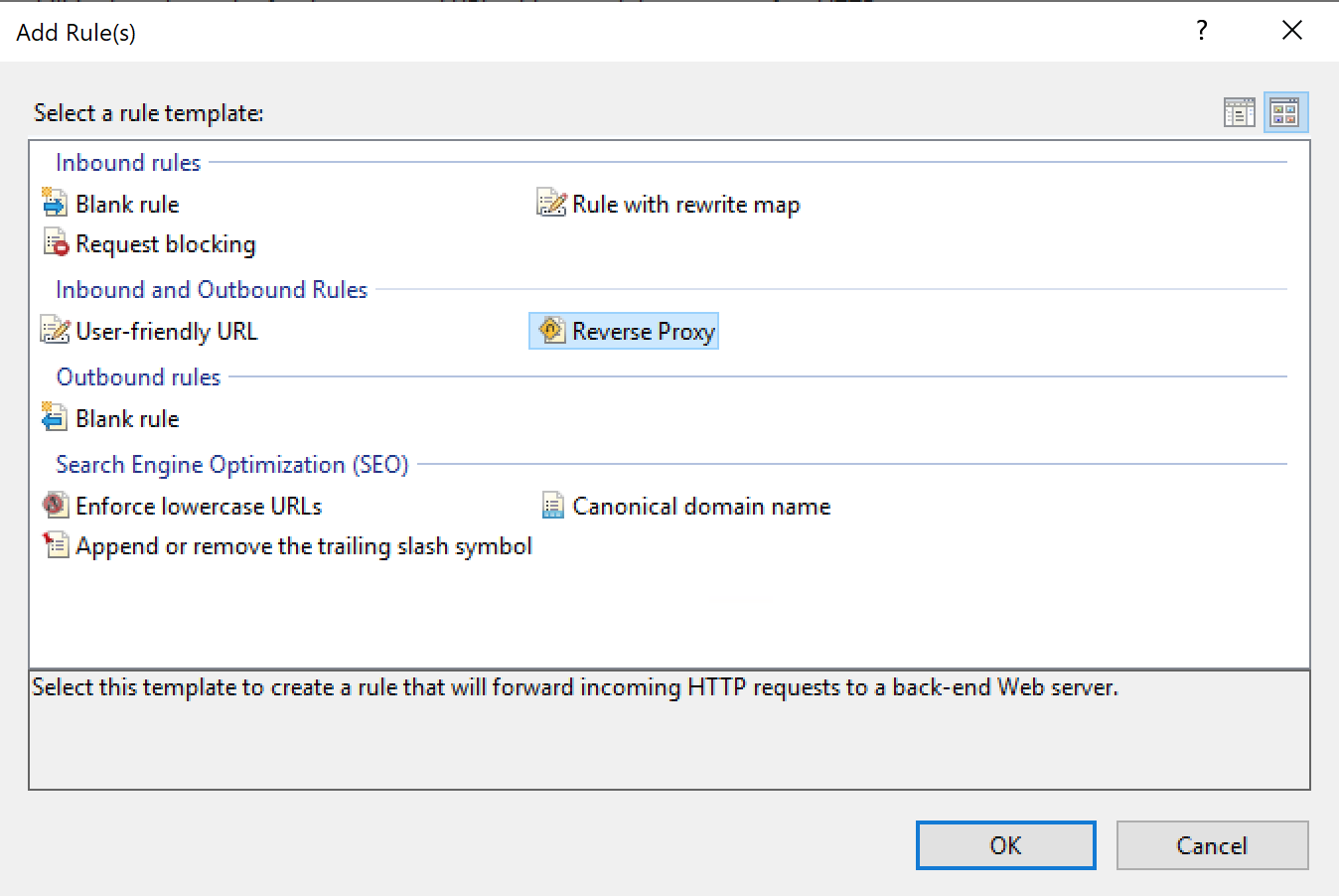
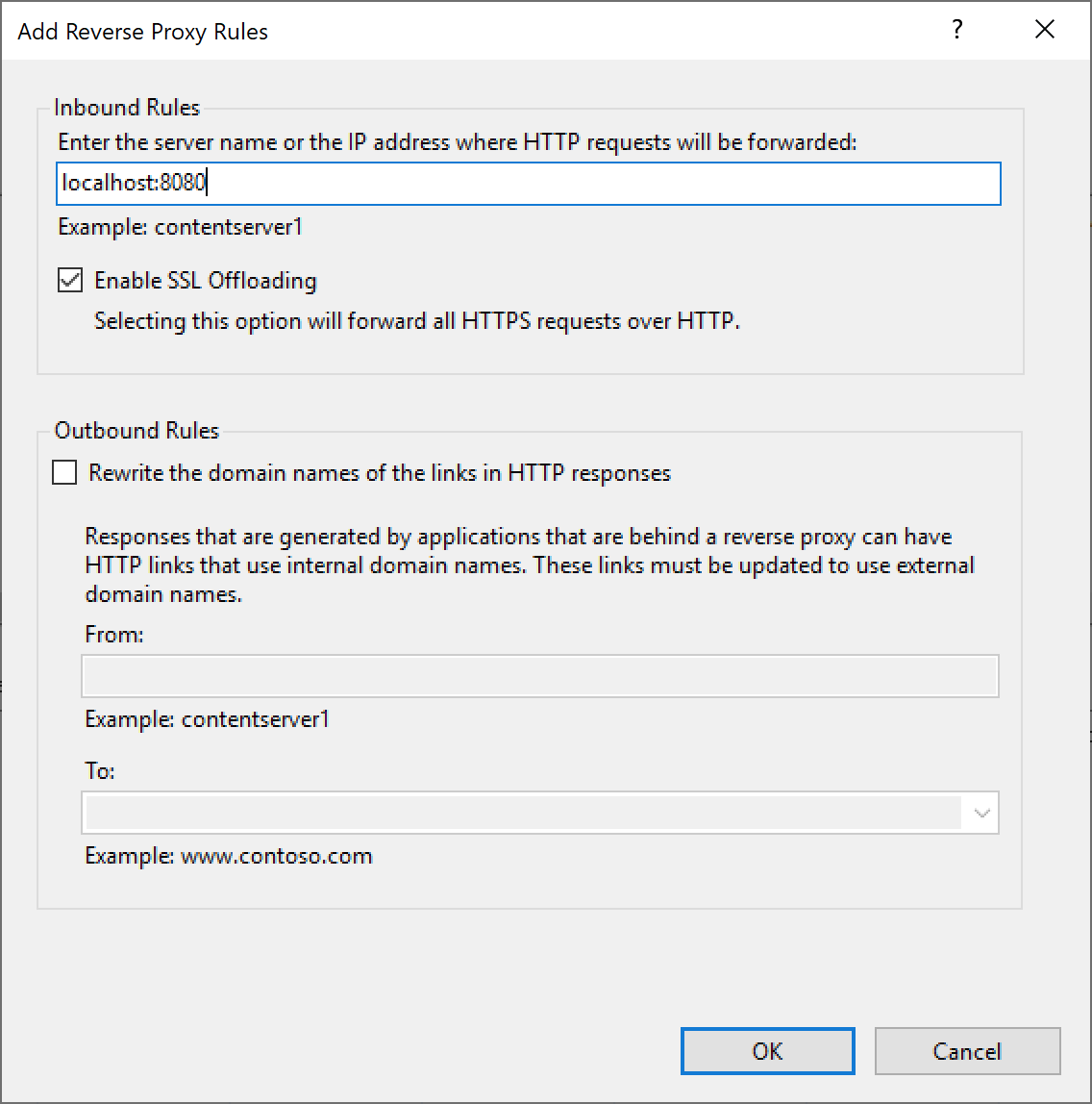
Select Reverse Proxy and the rule should end up similar to:
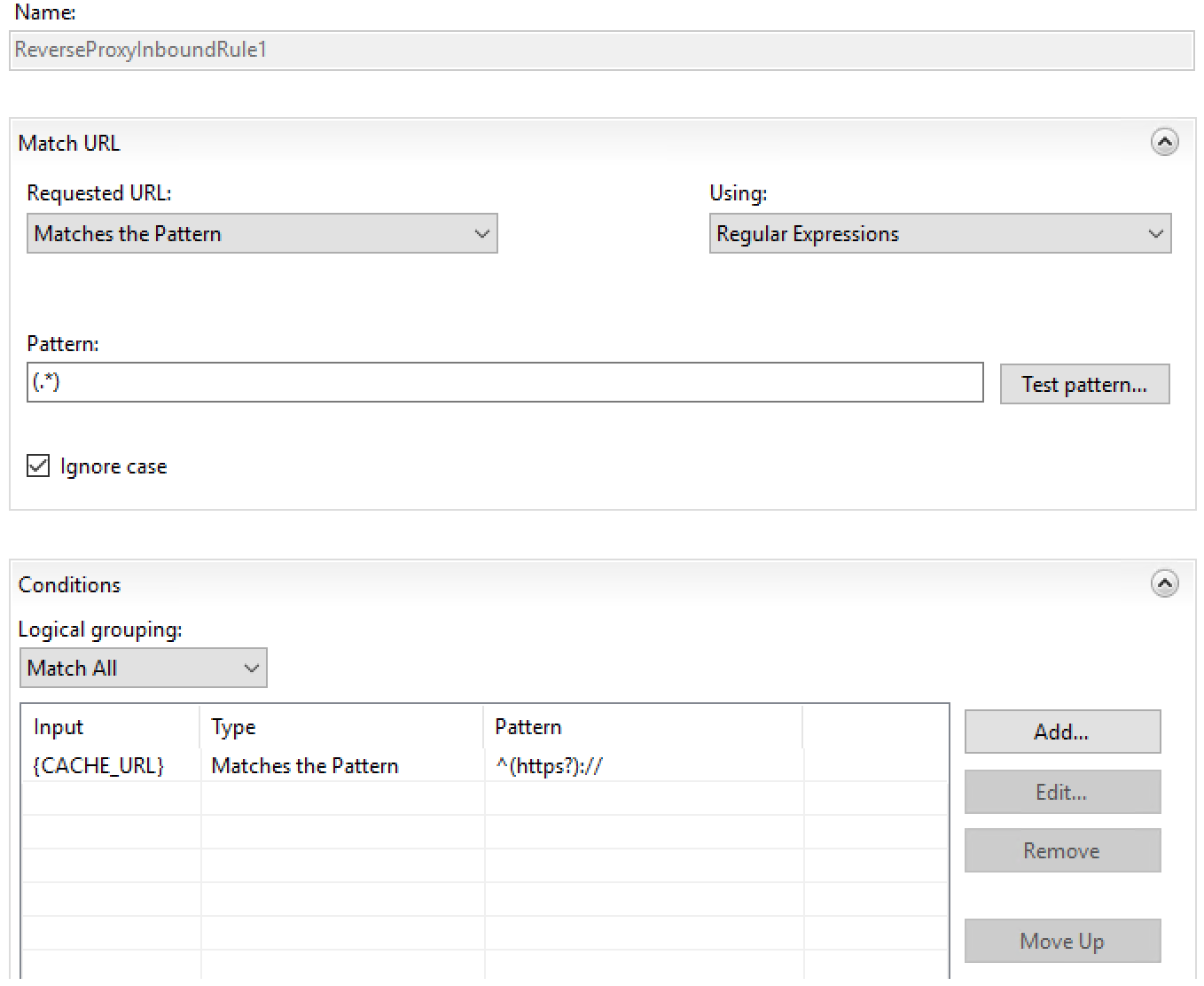
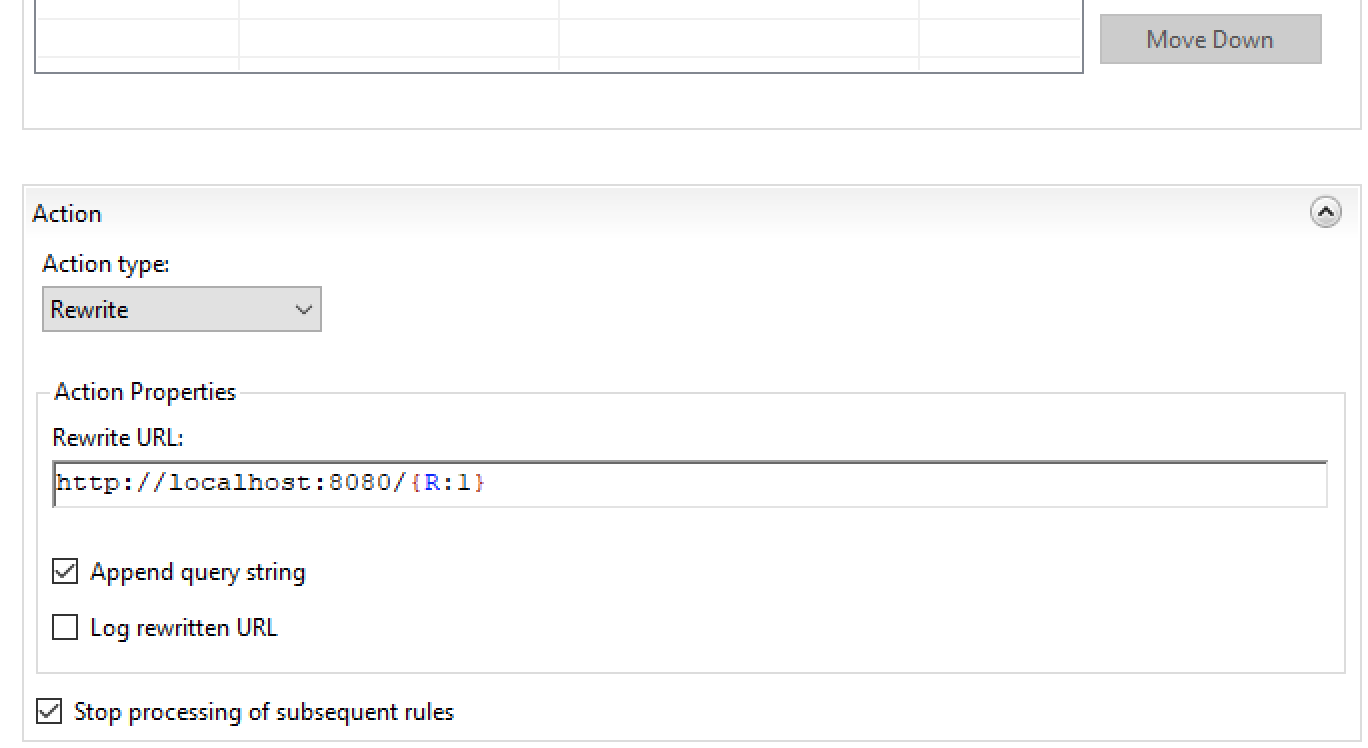
At this point the IIS reverse proxy tomcat is setup and configured.
Testing
With a web browser going to something like:
http://servername/ and https://servername:8080/
should have identical output. If this doesn’t work, the best place to start troubleshooting is with the Action part of the rewrite rule.
Security
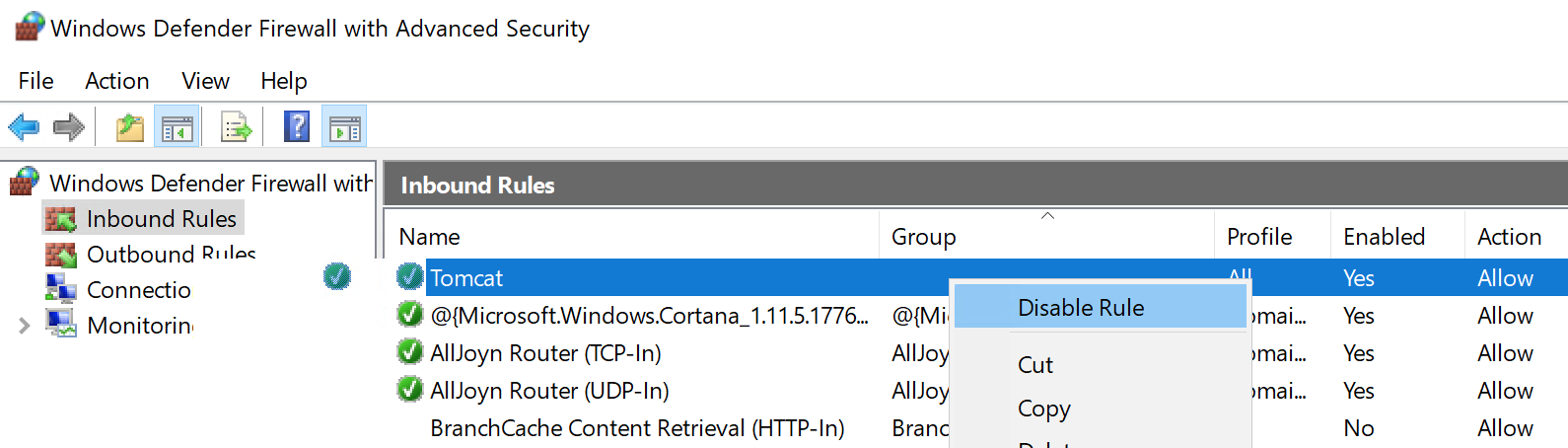
After testing has confirmed the reverse proxy is working as intended, we can do a few things to improve internet information server security. First remove the rule in Windows Defender File that allows access to port 8080. Note the rule may be named differently on another system.
SSL
Up to this point we have focused on non-encrypted connections to the web server, but the mostly likely scenario is using IIS to serve the pages via https.
A SSL certificate is required for https, which may already be in use with Tomcat, or one may need to be purchased/generated. We won’t go into much detail on setting up SSL, but generally it will be done through the IIS Manager as follows:
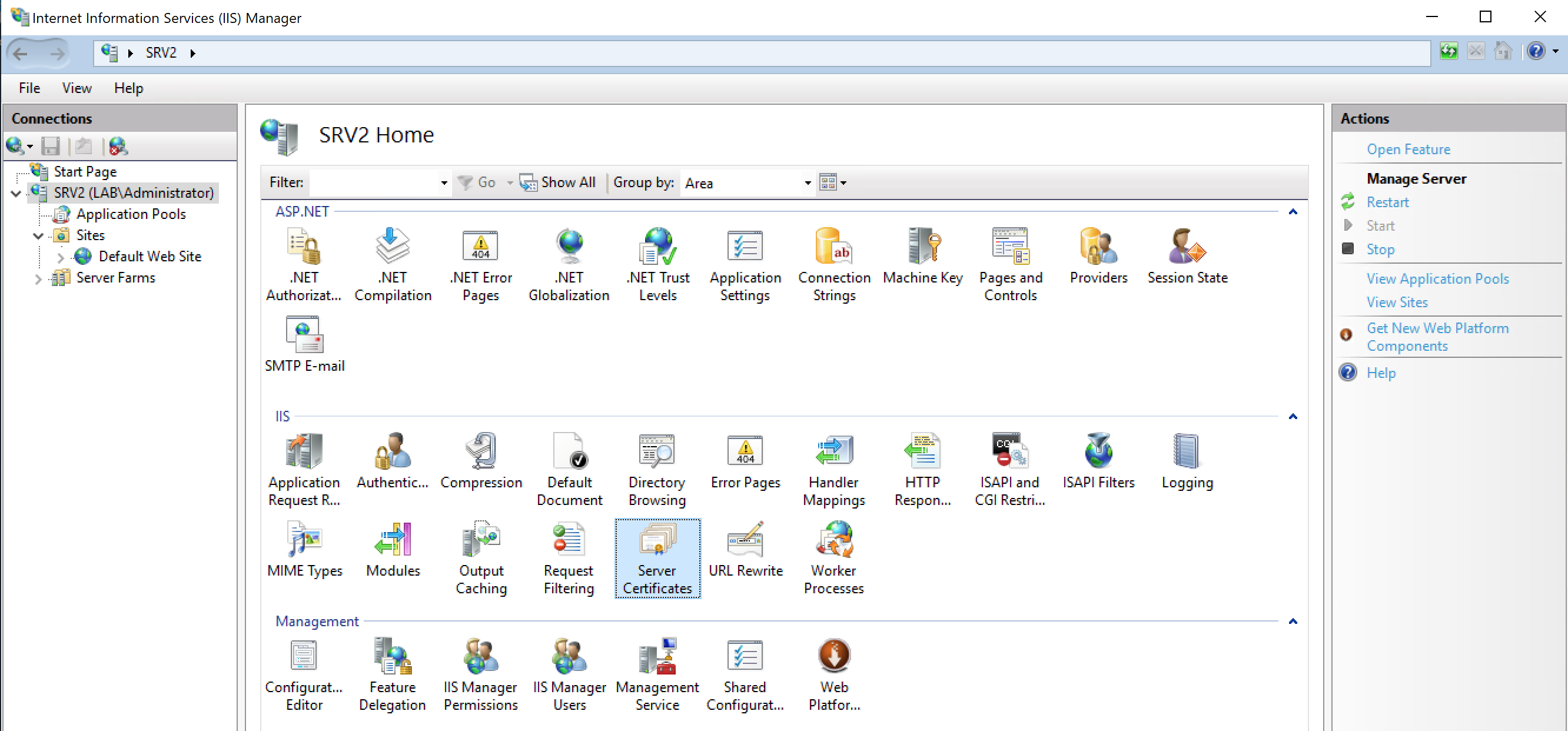
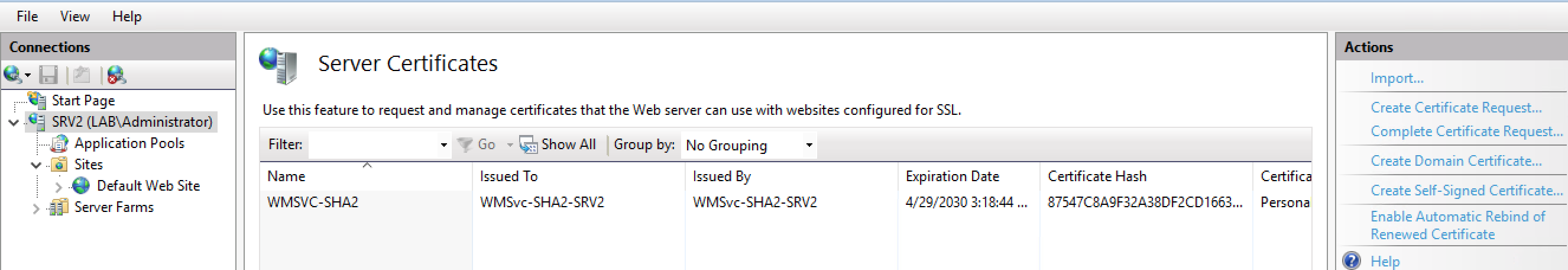
Once the certificate is installed, you need to edit site bindings…
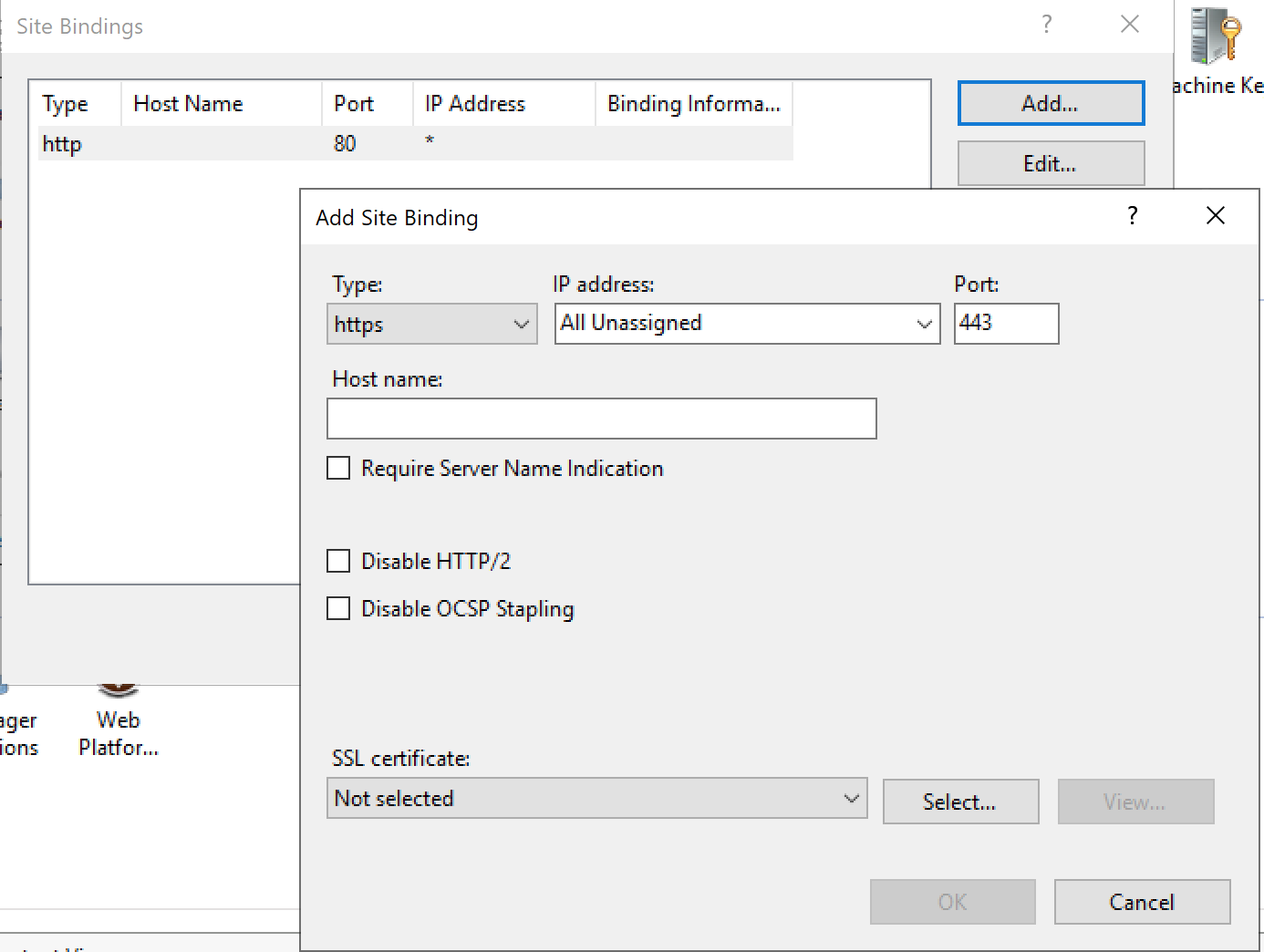
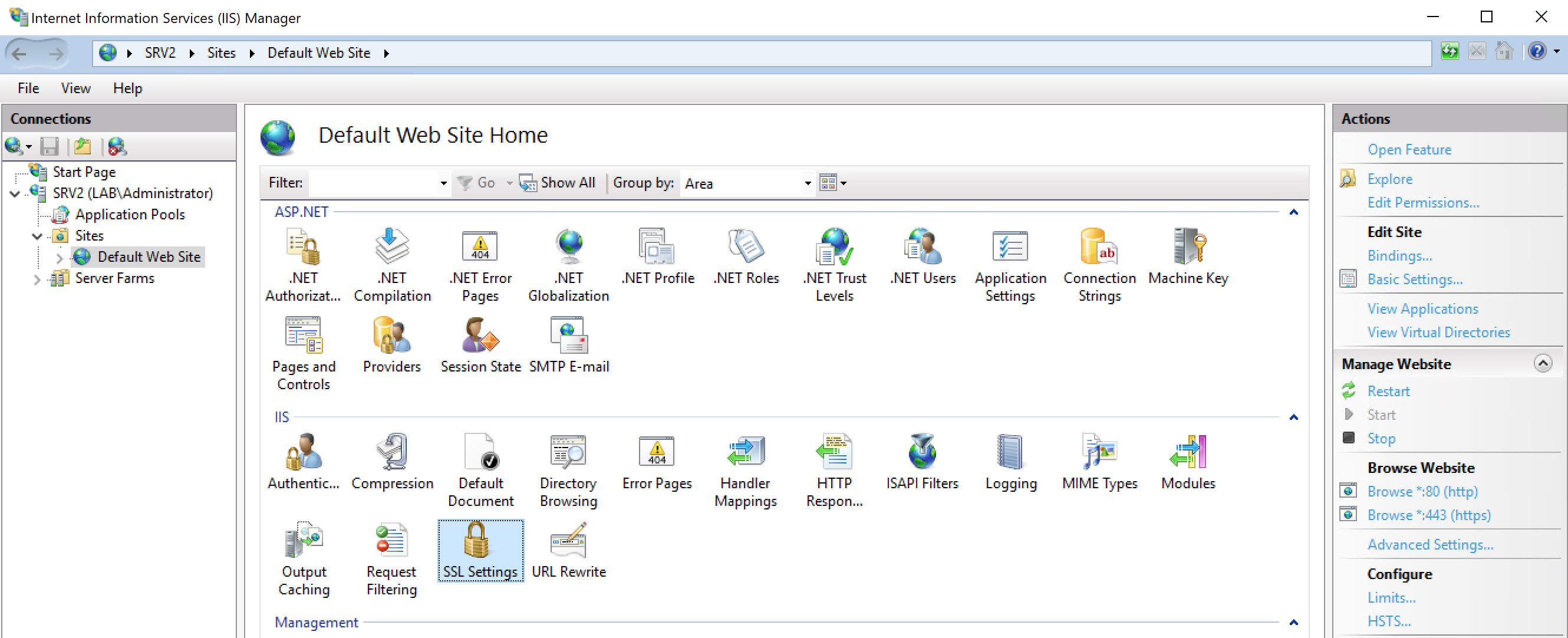
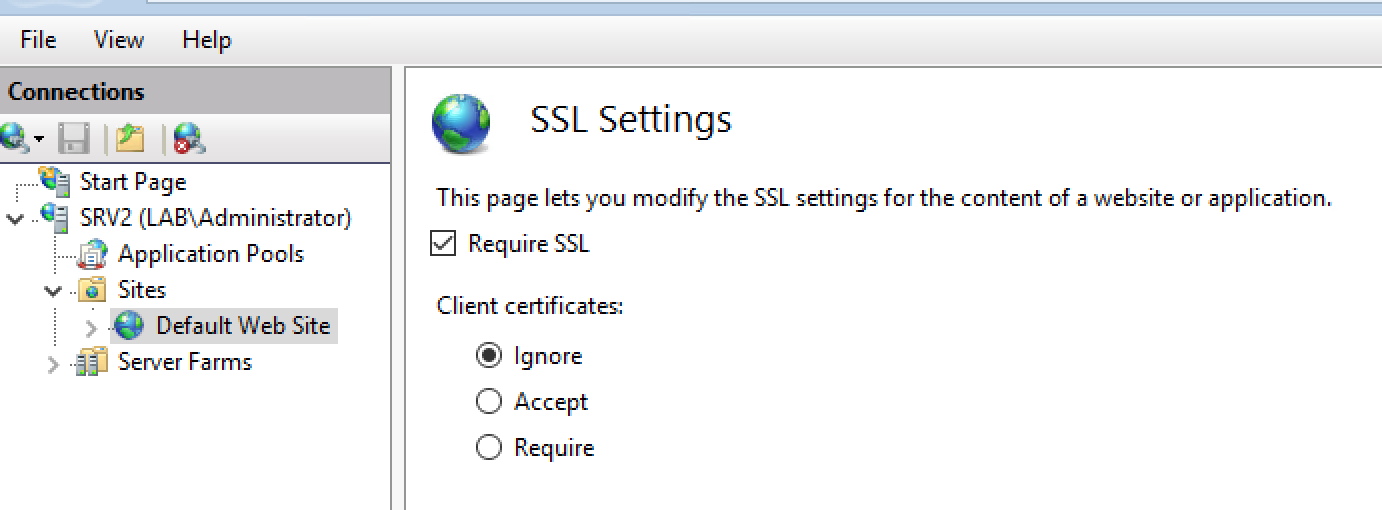
Restart the website. Now https connections should be allowed.
Disabling TLS 1.0/1.1
Microsoft has good documentation on TLS setting available here:
https://docs.microsoft.com/en-us/windows-server/security/tls/tls-registry-settings
The following registry changes can be a start, but further configuration of IIS should also be performed.
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server]
"Enabled"=dword:00000000
We hope this helps you. If you have any issues or questions, please contact us or schedule a FREE IT assessment today!
-1.png?width=350&height=117&name=iuvo_logo_blue_Transparent%20(1)-1.png)