It’s the New Year, which means it’s a great time to get organized. And if you’re struggling to get motivated on the really hard stuff—like mopping your floors or sorting through mismatched socks—try starting by organizing your digital files. You can...
Getting (Digitally) Organized in the New Year
by
Team iuvo |
January
10,
2023 |
Process,
Team,
Microsoft Office 365,
Remote Work,
compliance,
it consulting,
Teamwork,
microsoft,
How To,
Information Technology
Conditional Access Policies: Require MFA For Guests In o365 Tenant
by
Greg Brown |
January
19,
2021 |
IT Management,
Process,
Security,
IT Infrastructure,
Team,
Microsoft Office 365,
compliance
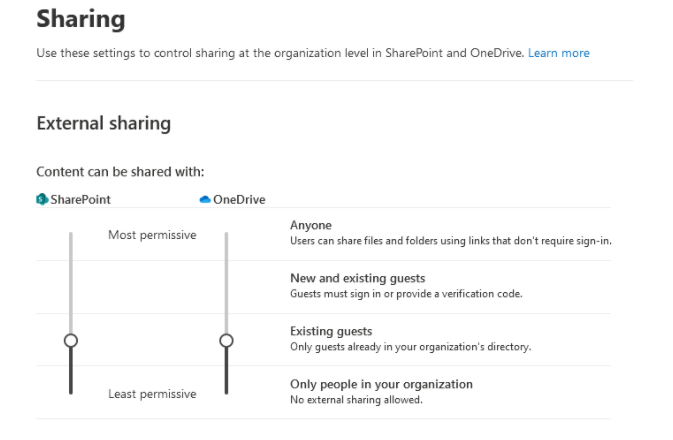
Your organization uses Sharepoint/OneDrive and works very hard to make sure all of your sensitive documents are secure and safe against any attackers or wrongdoers. Your IT Department has done what they think are all of the necessary things and have...
3 Steps for IT Compliance with Business Associate Agreements
by
Bryon Beilman |
October
20,
2020 |
IT Management,
Security,
IT Infrastructure,
biotech,
life sciences,
compliance
In the life sciences industry, partnerships with pharmaceutical companies often require signing business associate agreements (BAAs). What are these contracts, and how can your biotech startup prepare for opportunities that involve protected health...
A Guide to Rule-Based vs. Role-Based Access Control: What are the Differences?
by
Bryon Beilman |
March
28,
2019 |
IT Management,
Process,
Security,
IT Infrastructure,
IT Support,
cybersecurity,
Data Breach,
IT Services,
compliance,
it consulting,
#itstrategy
As you know, network and data security are very important aspects of any organization’s overall IT planning. When it comes to implementing policies and procedures, there are a variety of ways to lock down your data, including the use of access...
-1.png?width=350&height=117&name=iuvo_logo_blue_Transparent%20(1)-1.png)