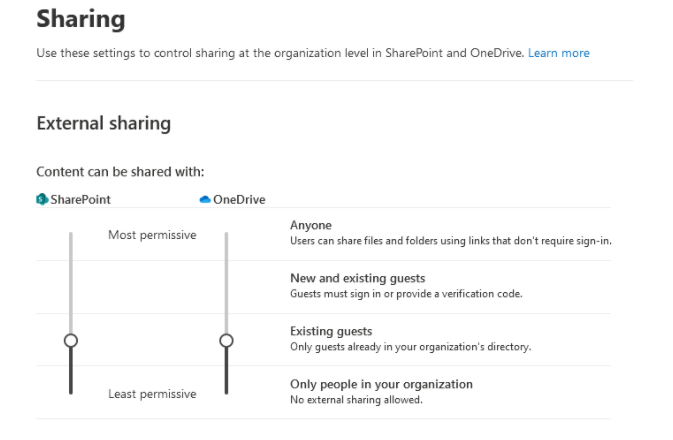
Your organization uses Sharepoint/OneDrive and works very hard to make sure all of your sensitive documents are secure and safe against any attackers or wrongdoers. Your IT Department has done what they think are all of the necessary things and have...
Conditional Access Policies: Require MFA For Guests In o365 Tenant
The Science of Chaos to Clarity
What do you do when your life is in Chaos? Perhaps you call a close friend, a family member, a mentor or an advisor and seek help. When things get to a state where the word chaos can be used, stopping to reflect and reach out may not be a luxury...
The Importance of Strong Vendor Relationships
Let’s start by thinking of a scenario in which you ran into an issue, small or large, and knew you needed to seek out help. I can certainly think of a few and can say the same for others. You most certainly are not alone in this.
CentOS Linux Version 8 On Windows Subsystem for Linux
We will look at setting up CentOS version 8 on Windows Subsystem for Linux (WSL). Due to certain issues with the Microsoft Store licensing there is not an officially supported and free version of CentOS available the way Ubuntu Linux is. We will...
Are Ransomware Attacks Data Breaches?
Everyone is familiar with, or has heard of, ransomware. It has been around in some fashion since 1989, with notable resurgence in 2005 and 2013. The original idea was to extort money from the victims by gaining access to their systems and encrypting...
-1.png?width=350&height=117&name=iuvo_logo_blue_Transparent%20(1)-1.png)