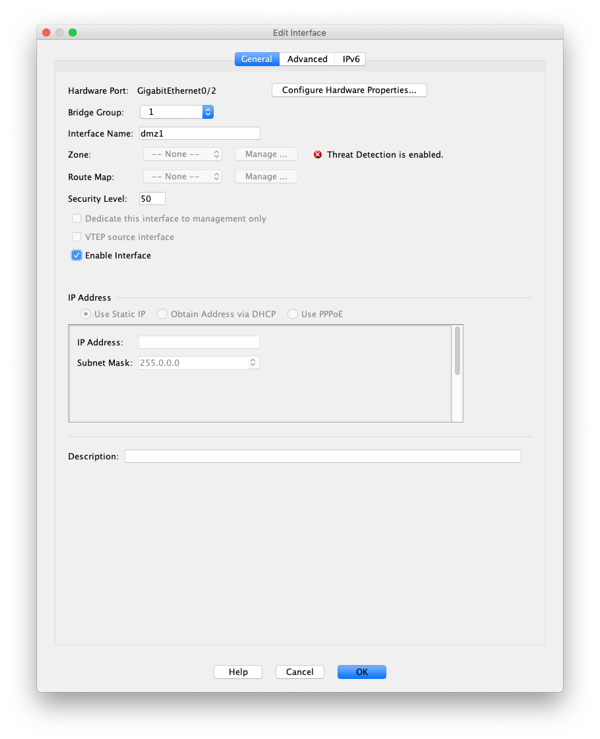
Port forwarding is a critical feature of any network firewall. The ability to provide a service to the Internet requires being able to forward ports from one interface of a firewall to another interface. Sometimes these services are on dedicated IP...
Port Forwarding with CISCO ASA and ASDM
Gradual Escalation in Vendor Escalation Management
I’m an author and one of the things you learn as a … writer… is to try not to repeat words, but I used “escalation” twice in the title of this post, and now I’m cringing. So, I shall now randomly expose you to a writer’s concept called “hanging a...
Documentation in Vendor Escalation
This is the sixth entry in this series on all the various complexities of managing vendor escalations. This one, however, is a super easy one. So fortunately- and rarely will you hear such a phrase from me- I can keep this one short.
The Importance of Being Available
In our previous post, we discussed the importance of maintaining the Moral High Ground and gave an example of the impact it can have on your support escalation adventures. In this post, we’re going to talk about the often-overlooked importance of...
A Guide to Rule-Based vs. Role-Based Access Control: What are the Differences?
As you know, network and data security are very important aspects of any organization’s overall IT planning. When it comes to implementing policies and procedures, there are a variety of ways to lock down your data, including the use of access...
-1.png?width=350&height=117&name=iuvo_logo_blue_Transparent%20(1)-1.png)